Offensive Security Penetration Testing with Kali Linux Review
Estimated read time: ~24 minutesOffensive Security’s Penetration Testing with Kali Linux (PWK) course is one of the most recognized ethical hacking and penetration testing courses within the information security industry. It made a name for itself and did so for good reason.
The course is known to be very practical, hands-on, and equal parts frustrating as well as difficult. Offensive Security does not want you to just know the theory, they want you to develop and demonstrate practical ability. Because of this the PWK course is not for everyone as the time commitment and persistence needed to pass can be off-putting for some individuals.
Offensive Security has a well-known mindset often expressed in two words that you will become quite familiar with sooner rather than later. Try Harder while sometimes misunderstood is as much a mindset as it is a motto and statement of encouragement. With the PWK course they try to instil this mindset in their own unique way.
Plan Comparison
Offensive Security offers the PWK course in three plans.
Each plan includes the 350+ page course guide, several hours of video content and an attempt at the Offensive Security Certified Professional (OSCP) exam. The only difference between the plans is the amount of time you have access to the student lab where you can practice the course exercises, develop your methodology and penetration testing skills.
While initially purchasing the course lab access can be purchased for thirty, sixty or ninety days, an exam voucher can also be purchased separately in case you fail the exam on your first attempt. Take note however that it is not possible to just purchase an exam voucher, you have to purchase the PWK course before you are allowed to take the OSCP exam.
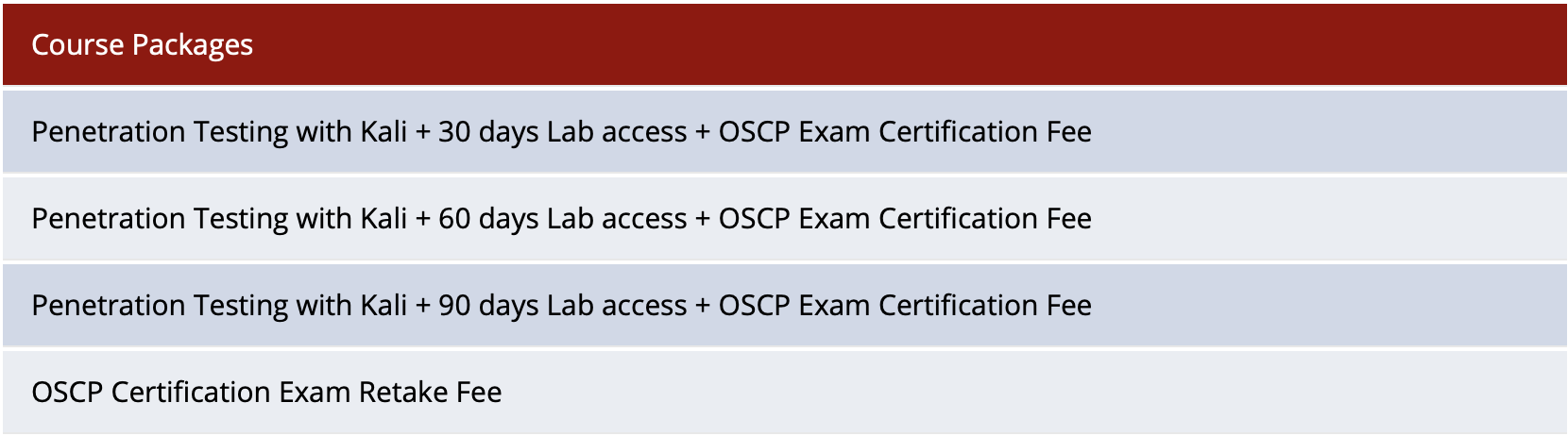
After initial purchase lab access can be extended in fifteen, thirty, sixty- or ninety-day increments offering a flexible way to extend if you feel you need more time to progress through the student lab.

When purchasing I opted for ninety days of lab access giving me plenty of time to work through the course materials and also spend a good amount of time within the student lab.
Registration and Purchasing
Offensive Security has a rather meticulous process for individuals that want to purchase the PWK course, using an application process that starts by filling out the student application form. When submitted you will receive an email from Offensive Security stating the course prerequisites, information about the course material, student lab and pricing. It also includes a unique course registration link should you decide to purchase the course.
When you enrol Offensive Security will verify your identity by using the email address you provided. In case email identity verification fails they will contact you and ask for an alternate email address or a copy of your passport or driver’s license.
If you want to avoid sending them a copy of either document you should use an email address containing your name and use a domain name owned by you, your employer or a university you attend to increase the chance of identity verification through email. Free email addresses such as Outlook, Gmail or Yahoo will not suffice.
For some reason Offensive Security was not able to verify my identity and they asked me for additional information. This process was very straight forward and it only took them a few hours to verify my additional details before I could enrol in the course.
Once your identity is verified you will receive a post registration email containing a link to a custom version of the Kali Linux operating system that Offensive Security recommends while working through the course materials and exercises. It also contains detailed information on how to perform a VPN connectivity test to the student lab. If the VPN connectivity test is successful you can proceed to make payment for the course.
When payment is received Offensive Security sends one more email confirming registration and also lists your start date for the PWK course. They will include a personal purchase link so you do not have to go through the registration process again if you wish to purchase other Offensive Security courses or a lab extension.
As stated before Offensive Security has their own meticulous process for individuals that want to purchase the PWK course. During the enrolment process they provide a lot of information about the course to make sure you know what you are getting yourself into.
Be advised that a waiting list of four to six weeks is not unheard of. Please keep this in mind if you want to enrol.
The Course Content
On your course start date you will receive an email containing several links to download the course guide, accompanying videos and a VPN connectivity pack to connect to the student lab. The email also contains information on how to connect to the student lab control panel and your personal virtual machine. This virtual machine is used for a multitude of course exercises and can come in handy while developing or testing exploits.
The course guide is split up in an introductory module, seventeen modules on penetration testing and the penetration testing process and a bonus module that combines all the content in an action-packed real-world penetration test for your entertainment and to solidify understanding. If you want more details on the course guide and what it covers the syllabus can be found here.
I appreciate that the course begins with the basics of Kali Linux and an introduction to scripting in both Bash and Python while following up with some essential tools like Netcat and Wireshark. For some this might be boring stuff but as the course is also geared towards less experienced individuals I really appreciate they put this in.
The exercises contained within the first few modules really help you feel more at home on the command line and make sure you know some of the tools that make up the swiss army knife of network troubleshooting and by extension penetration testing all without making it too complex to understand. While overlooked by many Netcat and Wireshark are incredibly versatile tools in your arsenal and skipping this part of the course is doing yourself a disservice in the long run.
The material also includes basic information gathering and enumeration techniques for various services before getting into the more exciting stuff such as stack based buffer overflows, privilege escalation, client side attacks and port redirection and tunnelling.
The modules on stack based buffer overflows and client side attacks while daunting at first are probably my favourites within the course along with the port redirection and tunnelling module. While it is hard to wrap your head around the last one when you first read through the module it all comes together once you start practicing it in the student lab. Understanding the techniques explained in this module opens up a world of possibilities. Once mastered you will never look the same way at that firewall or network design again.
While it is tempting to jump straight into the more interesting looking modules or skip the course material all together and jump straight into the student lab I recommend against this unless you are an experienced penetration tester. The content is very well laid out and beginning with the first module and working through it until the end is probably the best course of action for beginners.
The Videos
The videos accompany the course content very well and are usually short and to the point focusing on the task at hand without adding fluff. This is ideal if you want to reference something later as you do not have to skip through long videos to find what you are looking for.
Some of the trainer’s dry comments after successfully completing an exercise or task are also quite hilarious and once you heard them you start to appreciate them throughout the remaining video content. They will make you laugh more than once in the eight hours of video available.
The Exercises
There are plenty of exercises spread throughout the course material, some easier than others and most of them depend on access to either your virtual machine or the student lab.
I highly recommend doing the exercises as they solidify your understanding and help you to get to know the lab environment and some of the vulnerable machines within it. This will give you a starting point to compromise your first machines. If you do decide to jump straight into the lab and become frustrated with your progress go back to the course material and exercises as you are in over your head.
The exercises can also be appended to a lab report should you decide to make one which is advisable because it gives you the opportunity to earn five additional bonus points for the OSCP exam.
The Lab
The student lab is the bread and butter of the PWK course and a living environment containing various different operating systems and vulnerable software.
The lab also spans several different networks and contains multiple automated users and machines that are dependent on one another in such a way that some of them cannot be compromised without valuable information found elsewhere in the lab. Contrary to popular belief this lab is not just a Capture the Flag with to goal to get root or system level privileges as fast as possible and move on, approach it as such and you are going to have a bad time.
While working through the lab you start to notice a lot of care has been taken to put it together and develop it. There are several well placed hints for those who are looking and while most of the systems and software are a bit older and exploits are readily available this lab is still no walk in the park. Offensive Security has its own methods to add a little twist here and there making sure you start thinking out of the box instead of just firing off exploits and winning.
Like many others before you, you will encounter your fair share of frustration, mental breakdowns and sometimes start to question your sanity while on your travels through the lab. The feeling when you finally do root that box or find that valuable piece of information to move forward after days of trying is an incredible feeling though.
While tempting to save time, money or both completing only part of the student lab while probably enough to pass the exam is a waste. If you have not compromised several boxes in the multitude of adjacent networks along with a substantial portion of the student network I highly recommend extending your lab time, not because you could not pass the exam, you probably could but because there are so much more valuable lessons to learn.
The lab is quite addicting and once you complete the course and the OSCP exam you start to miss it. While you can go back to complete those machines you did not compromise after completing the OSCP exam you probably won’t so take your time in the lab leaving no stone unturned!
The Lab Report
If you value the five bonus points mentioned earlier you are encouraged to document and report the findings of your lab adventures back to Offensive Security in a professional lab report. The lab report should contain your findings and a walk-through including proof of no less than ten compromised machines. Each machine should be compromised through a unique vulnerability. Using the same vulnerability twice on different machines will not count. The lab report should also contain documentation on all of the course exercises as an appendix.
In the end I did not submit a lab report with my exam documentation mostly due to reasons stated below. If you decide not to submit the report for the five bonus points I still highly recommend documenting ten machines while using the template Offensive Security provides as it is good practice for the reporting portion of the exam. You do not want to start figuring out the template and reporting requirements after you just had a gruelling twenty-four-hour exam and need to document your findings.
Study Method
My study method during the course followed a simple approach:
- Watch the video of a certain piece of content
- Read the content in the accompanying course guide
- Do the exercises referencing the video and guide where needed
- Make notes where needed for later reference
Combining all the course material in this way worked well for me and made sure I was not getting bored doing just one part of the materials. In some cases, I went a bit beyond the exercises and tried my luck in the student lab attacking a box here and there.
In the beginning of the course I made sure to go back to the approach mentioned above, the lab is addicting though and I spend more and more time in the lab neglecting the last few exercises I had left. While I don’t regret this, it did result in several hours of frustration on boxes that I could have compromised in a lot less time had I followed my own approach above and did the exercises.
It also resulted in the decision to not submit a lab report with my exam documentation as I ran out of lab time to finish the remaining exercises losing out on the five bonus points that could be earned.
Study Tips
Let me start by stating the following very important piece of advice: The PWK and the road to OSCP is a journey not a destination. For most the journey will not end with obtaining the OSCP certification if you want to pursue a career in this field. Do not hurry through this course, put in the time and effort to give yourself a solid foundation, you will be glad you did in the end.
Adding to the above statement the most valuable skills you will develop during this course are not how to compromise boxes nor will you learn the latest hacking techniques instead the most valuable skills you will develop are methodology and mindset. They will stay with you for the rest of your career and are incredibly valuable.
If you are new to this field you will get stuck somewhere eventually and feel defeated or frustrated about your progress on a box, the lab in general or how your methodology is failing you. This is normal and will teach you valuable lessons. Failing is part of learning and being stuck on a box for hours or sometimes even days is not a shame nor a problem. Remember the try harder mindset, embrace it and in time you will progress through the lab cracking it box by box, user by user and network by network.
While some advice to avoid the student forums I am not a fan of this advice. You cannot look for or educate yourself on topics or techniques you don’t know even exist and sometimes a little hint is all you need to start your search in the right direction and see that path forward to solve the challenge that lays before you. I will advise however to use the forums sparingly and as a last resort as most of what you have to know really is in the course guide and accompanying videos.
A more intuitive way to use the student forums is to gain information on other ways to compromise a target once you have the highest privileges possible. If you look well enough and read between the lines you can often get a glimpse into minds and methods of your fellow students and most likely learn something new from those perspectives.
Learning to document and make notes is a skill you will develop while working through the course materials and the lab. If I look back at notes of the first boxes I compromised they were honestly not all that good compared to later in the course. While following a template such as this one is a very good way to kickstart your documentation and note taking methodology refining it towards your own preferences as early as possible is a very good idea and worth putting time and effort in.
Knowing the above here is some more advice you should take to heart:
- Enumerate, enumerate, enumerate! Did I say enumerate?
- Become comfortable with and learn to pivot in the labs
- Stuck in the lab? You probably did not enumerate enough!
- Work on your documentation immediately after compromising a machine
- Do not skip the exercises if you are just getting started in this field
- Stuck on a box for hours? Skip it and come back later, it might very well have a dependency
- Document ten or more boxes, even if you do not want to submit a lab report. It is valuable practice for the exam
- Take your time in the student lab, gaining experience from all the boxes is the most valuable part of the course
- Spend some time looking through a box once you fully compromised it, there might be information you can use to your advantage
- Take some time in the lab to develop your documentation and reporting skills like hacking boxes it is part of what you have to learn
Exam Proctoring
In July of 2018 Offensive Security announced exam proctoring for the OSCP exam. While this decision was received with mixed feelings by the information security community I am of the opinion that it is the right decision if strengthens the integrity of the OSCP exam and certification in the long run.
I did my OSCP exam on the 30th of May which means I was subject to a proctored exam. Overall the process was very straight forward. Before starting the exam, you have to turn on your webcam by way of navigating to a website and start a webcam session so the proctors can monitor you and your surroundings.
You also have to install a program so the proctors can view all your connected screens. The proctors will verify your identity by checking your passport through the webcam and ask you to show the room in which your will perform your exam. Once al pre-exam verification is completed the proctors will release your exam and you will receive your exam information and exam VPN connectivity pack by email. All this takes about fifteen to twenty minutes so make sure you are ready about half an hour before your exam starts.
In the beginning of your exam it is a very strange feeling to be continually watched. I felt more at ease after an hour or so and a couple of hours in you won’t even notice someone is monitoring your every move. The proctors are very polite and professional and some of their names (they use aliases) are pretty funny to see once they pop up in the chat window.
While you are performing your exam, you can take breaks as much as you want, as long as you want. You can also sleep during the exam. All as long as you inform the proctors when you are going on a break and when you come back. They will sometimes ask you to refresh the webcam page, for me this was usually after I came back from a break so it did not interrupt my exam experience in a negative or meaningful way.
I would strongly advice against it, as you need your focus on the exam but having a significant other, children or other family members of the household in the room while you are performing your exam is also not a problem, just inform the proctors so they know in advance.
The Exam
I have a whole lot of mixed feelings about this exam, it is long, it is exhausting, it is frustrating at times. It is an emotional roller coaster when you get your first shell, when you root a box and simultaneously get a slap in the face because you get stuck for several hours on another one and bang your head against your desk because you do not see a solution for the problem while it is most likely right in front of you.
On the other hand, looking back at all of it, it was very doable in the twenty-four hours Offensive Security gives you and in the end I even had some time to sleep and double, even triple check my documentation to make sure I had everything needed to write my exam report the next day.
Box One
I started my exam at exactly 14:00 GMT immediately focusing my attention on the box known to have a stack based buffer overflow vulnerability, developing my Proof of Concept and exploiting the machine while making my documentation along the way.
I practiced the BoF process till I could do it with my eyes closed and the time invested paid off big time as I submitted the proof to the exam control panel around 16:00 compromising the box in about two hours flat and the added benefit that a substantial portion of my documentation was already done.
Box Two
After this I focused my attention on the second high point box and while I identified a possible entry point rather quickly I could not get it to work at first. After about an hour and a half of trying my moral was down and I started to focus my attention on the lowest point box.
Box Three
This box was a fun challenge. After some through enumeration I found an exploit for a piece of software. With some fiddling and trial and error I was rewarded for my efforts and submitted proof of my success to the exam control panel around 19:30.
Box Four and Five
After compromising the low point box morale was up and I started enumerating both middle of the pack point boxes looking for a clue on which box I should focus my attention next. Something on one of the boxes caught my eye and I started to focus on it while my enumeration kept running on the other box.
Box Four
Hello enumeration, my old friend! My true and trusted methodology was the only thing saving my ass while taking on this box.
I am sure I would have failed the exam had I not trusted in it religiously after it helped me countless times in the labs. The box finally fell around 22:00 and I submitted the proof with a big smile on my face in the exam control panel.
Box Two (Again)
With two boxes to go and a hunch for a shell on the second high pointer I started to poke at it once again and around 23:00 I gained a shell on the box.
I tried escalating privileges for about an hour but with three boxes rooted and a low privilege shell on this one I decided to notify the proctors that I was going to get some sleep and called it a night around 00:00.
Box Five
I woke up around 05:00 in the morning knowing what I had to do. I took some coffee and told the friendly proctors who were waiting for me that I was back at it.
Having compromised three boxes and with a low privilege shell on the second high pointer I quickly reviewed the enumeration I started on box five the night before and decided to use my Metasploit attempt. Partly because I saw no added benefit to use it on the second high pointer and also because I wanted quick results on box five.
I could not suppress my excitement when the box stopped resisting my almost perfectly planned efforts. He was done for, I won! I submitted the proof of my endeavours with box five around 06:30 realising I had enough points to pass.
Box Two (Attempt Three)
With four boxes rooted and a low privilege shell on the second high pointer I started trying to escalate privileges on this box again. After banging my head against this for several hours without results I decided to accept my defeat and started focusing on my documentation instead.
I went through the BoF again triple checking everything. Collected my payloads and the commands used to compromise the other boxes, tested them again and made sure I had all the proof and screenshots needed.
At 12:00 I checked everything again and was tired enough to ask the proctors if I could end my exam early. They were polite and understanding, asked me if I was sure, I confirmed and thanked them for staying with me all this time.
I went for a quick sleep, knowing I most likely passed if I did not screw up royally on my documentation efforts.
The Exam Report
When I woke up just a few hours later I started documenting all my findings. I used a modified version of the Offensive Security report template that I mostly prepared in advance and already contained the documentation on my efforts with the BoF box so I only had to fill in the blanks on the other boxes.
I kept refining the report and checked time and time again if it fit the reporting requirements almost paranoid to make a mistake. I finally submitted the exam report at 09:30 on the 1st of June. Offensive Security sent a confirmation they received my documentation about two hours later, and so the waiting game begins!
Confirmation, I Passed
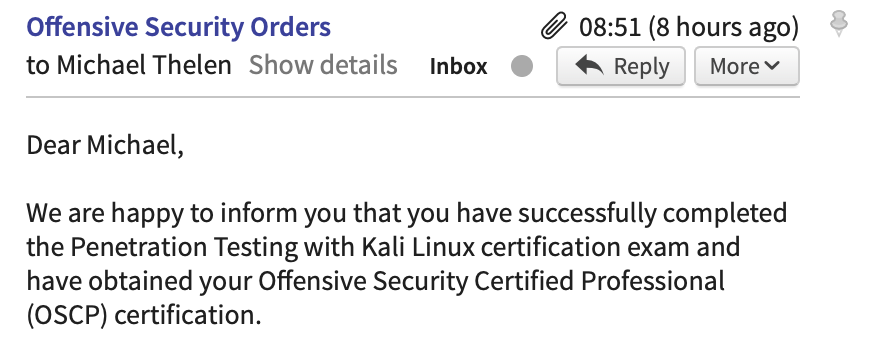
It took Offensive Security a few days to review my exam documentation but on the morning of the 6th of June I finally received that email that I had been waiting for and gives you that incredible feeling of relief, I had passed the OSCP!
Exam Tips
Try to unplug and have a good night’s rest on the day before the exam. Try and get some of those nerves under control on exam day, walk into the exam with confidence, think of it as nothing more than the lab where you spent all those hours learning what you know.
That said I can’t stress enough how important having a solid methodology is to passing this beast. Religiously develop, document and refine your methodology while doing the course exercises and during your time in the labs. Whatever you do during the exam, stick to your own tried and true methodology. No last-minute changes in tools, modifications to scripts or documented enumeration commands. Stick to what you know, when you grow frustrated, tired or feel down during the exam it is the only reliable friend you can depend upon.
Some people prefer to start early in the day and go at it for hours, others like to start a bit more towards the middle of the day or late at night. All I can say here is pick a time that works for you. When I scheduled my exam, I took a time slot starting at 14:00 GMT. I intended to have three blocks of eight hours to do the practical part of the exam without disturbing my normal sleep pattern too much.
- 14:00 > 22:00 Exam
- 22:00 > 06:00 Sleep
- 06:00 > 14:00 Exam
This left me with sixteen hours to compromise the boxes and while I obviously did not succeed in keeping the exact schedule above it still helped me to get a couple of hours of sleep. I am convinced this helped me think clearly the next day with my attempts on box five.
Some other important things to keep in mind:
- Take regular breaks and drink enough water
- This is a battle of enumeration, leave no stone unturned
- Sleep! Trust me just do it even if it is only a few hours
- Take your time for the buffer overflow, triple check everything
- Save any payload commands you use, you need them for your report
- Do not fear proctoring it is not as bad as you think or read online
- Take proof screenshots immediately after gaining a user or root shell
- Submit the proof flags in the control panel immediately once you obtain them
- Enjoy the exam, like the lab it is a really fun challenge once you get your nerves under control
- Prepare a template penetration test report that you can use to document during and after the exam
Also remember that failing is part of learning and while it is an awesome feeling to pass on the first try in the worst case you fail, learn something from the experience, refine your methodology and come back stronger and more prepared to try again!
Conclusion
The PWK course might be somewhat outdated in the opinion of some and while there might be some merit or truth to this statement I am a firm believer that one should have a firm grasp of the basics and a solid foundation first and foremost.
In my opinion the course succeeds in laying this foundation, a foundation you can trust and build upon to learn more complex topics faster than you would without it.
Above all else the course not only teaches you technical skills. It also teaches you persistence, mindset and methodology, skills that are of incredible value should you choose to pursue a career in the information security field or any other.
After the PWK course you will never think or look at a computer, computer network or piece of software the same way you did before but always have this little voice in the back of your head looking at it from another angle. How can I break it, how can I manipulate it, how do I get this “feature” to do my bidding instead of taking the way it works for granted.